If you’re a security, network, or IT leader, you’ve most likely heard the terms Zero Trust, Secure Access Service Edge (SASE) and Secure Service Edge (SSE) used to describe a new approach to enterprise network architecture. These frameworks are shaping a wave of technology that will fundamentally change the way corporate networks are built and operated, but the terms are often used interchangeably and inconsistently. It can be easy to get lost in a sea of buzzwords and lose track of the goals behind them: a more secure, faster, more reliable experience for your end users, applications, and networks. Today, we’ll break down each of these concepts — Zero Trust, SASE, and SSE — and outline the critical components required to achieve these goals. An evergreen version of this content is available at our Learning Center here.
What is Zero Trust?
Zero Trust is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside the network perimeter. This is in contrast to the traditional perimeter-based security model, where users are able to access resources once they’re granted access to the network — also known as a “castle and moat” architecture.
More simply put: traditional IT network security trusts anyone and anything inside the network. A Zero Trust architecture trusts no one and nothing. You can learn more about Zero Trust security here.
What is Secure Access Service Edge (SASE)?
Gartner introduced SASE as the framework to implement a Zero Trust architecture across any organization. SASE combines software-defined networking capabilities with a number of network security functions, all of which are delivered from a single cloud platform. In this way, SASE enables employees to authenticate and securely connect to internal resources from anywhere, and gives organizations better control over the traffic and data that enters and leaves their internal network.
The Secure Access component of SASE includes defining Zero Trust security policies across user devices and applications as well as branch, data center, and cloud traffic. The Service Edge component allows all traffic, regardless of its location, to pass through the Secure Access controls — without requiring back hauling to a central “hub” where those controls are enforced. You can learn more about SASE here.
What is Security Service Edge (SSE)?
SSE, also coined by Gartner, is a subset of SASE functionality specifically focused on security enforcement capabilities. It is a common stepping stone to a full SASE deployment, which extends SSE security controls to the corporate Wide Area Network (WAN) and includes software-defined networking capabilities such as traffic shaping and quality of service. You can learn more about SSE here.
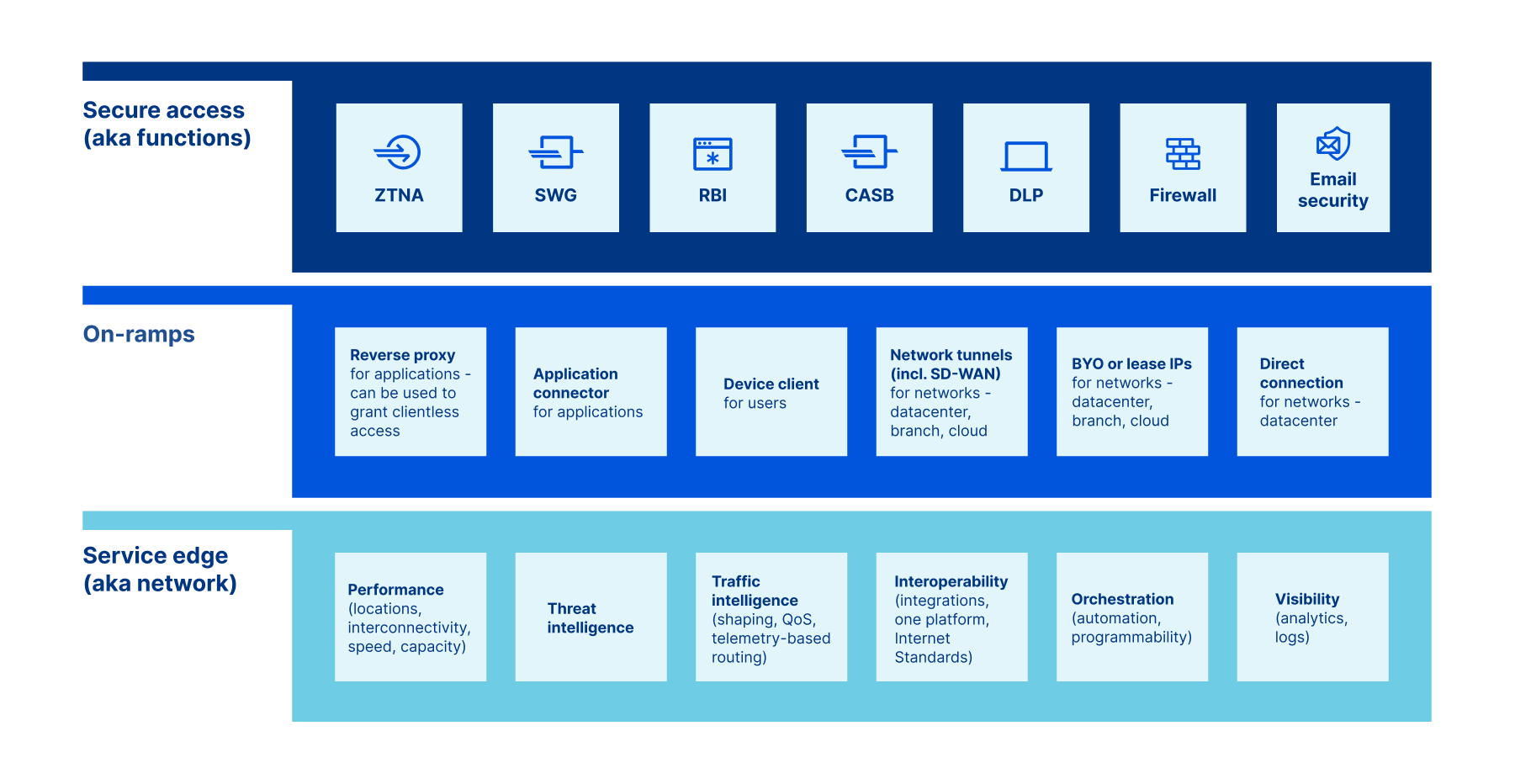
What makes up SASE?
The most commonly available definitions of SASE list a number of security functions like Zero Trust Network Access (ZTNA) and Cloud Access Security Broker (CASB), focusing on what a SASE platform needs to do. Security functions are a critical piece of the story, but these definitions are incomplete: they miss describing how the functions are achieved, which is just as important.
The complete definition of SASE builds on this list of security functions to include three distinct aspects: secure access, on-ramps, and service edge.
Cloudflare One: a comprehensive SASE platform
Cloudflare One is a complete SASE platform that combines a holistic set of secure access functions with flexible on-ramps to connect any traffic source and destination, all delivered on Cloudflare’s global network that acts as a blazing fast and reliable service edge. For organizations who want to start with SSE as a stepping stone to SASE, Cloudflare One also has you covered. It’s completely composable, so components can be deployed individually to address immediate use cases and build toward a full SASE architecture at your own pace.
Let’s break down each of the components of a SASE architecture in more detail and explain how Cloudflare One delivers them.
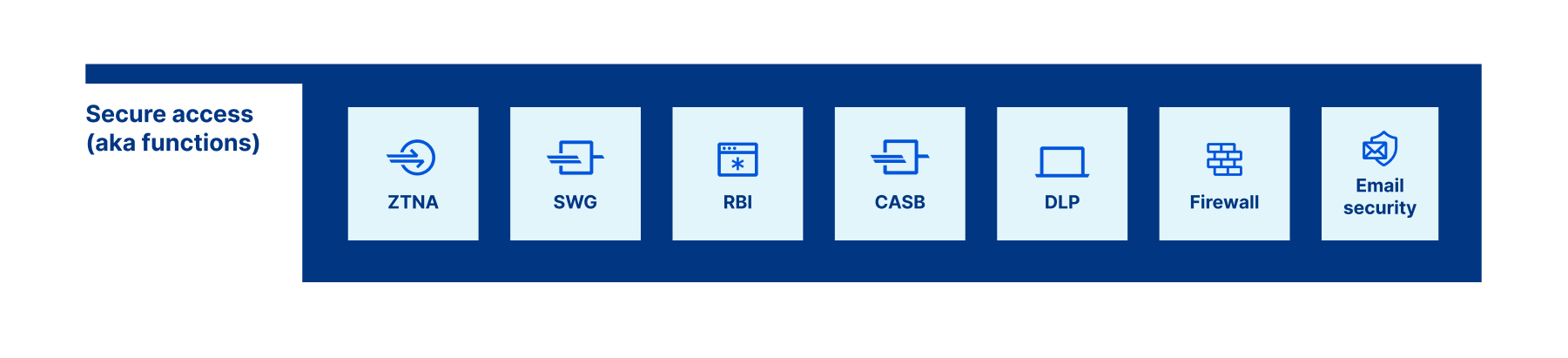
Secure access: security functions
Secure Access functions operate across your traffic to keep your users, applications, network, and data secure. In an input/process/output (IPO) model, you can think of secure access as the processes that monitor and act on your traffic.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access is the technology that makes it possible to implement a Zero Trust security model by requiring strict verification for every user and every device before authorizing them to access internal resources. Compared to traditional virtual private networks (VPNs), which grant access to an entire local network at once, ZTNA only grants access to the specific application requested and denies access to applications and data by default.
ZTNA can work together with other application security functions, like Web Application Firewalls, DDoS protection, and bot management, to provide complete protection for applications on the public Internet. More on ZTNA here.
 Cloudflare One includes a ZTNA solution, Cloudflare Access, which operates in client-based or clientless modes to grant access to self-hosted and SaaS applications.
Cloudflare One includes a ZTNA solution, Cloudflare Access, which operates in client-based or clientless modes to grant access to self-hosted and SaaS applications.
Secure Web Gateway (SWG)
A Secure Web Gateway operates between a corporate network and the Internet to enforce security policies and protect company data. Whether traffic originates from a user device, branch office, or application, SWGs provide layers of protection including URL filtering, malware detection and blocking, and application control. As a higher and higher percentage of corporate network traffic shifts from private networks to the Internet, deploying SWG has become critical to keeping company devices, networks, and data safe from a variety of security threats.
SWGs can work together with other tools including Web Application Firewalls and Network Firewalls to secure both inbound and outbound traffic flows across a corporate network. They can also integrate with Remote Browser Isolation (RBI) to prevent malware and other attacks from affecting corporate devices and networks, without completely blocking user access to Internet resources. More on SWG here.
 Cloudflare One includes a SWG solution, Cloudflare Gateway, which provides DNS, HTTP, and Network filtering for traffic from user devices and network locations.
Cloudflare One includes a SWG solution, Cloudflare Gateway, which provides DNS, HTTP, and Network filtering for traffic from user devices and network locations.
Remote Browser Isolation (RBI)
Browser isolation is a technology that keeps browsing activity secure by separating the process of loading webpages from the user devices displaying the webpages. This way, potentially malicious webpage code does not run on a user’s device, preventing malware infections and other cyber attacks from impacting both user devices and internal networks.
RBI works together with other secure access functions - for example, security teams can configure Secure Web Gateway policies to automatically isolate traffic to known or potentially suspicious websites. More on Browser Isolation here.
 Cloudflare One includes Browser Isolation. In contrast to legacy remote browser approaches, which send a slow and clunky version of the web page to the user, Cloudflare Browser Isolation draws an exact replica of the page on the user’s device, and then delivers that replica so quickly that it feels like a regular browser.
Cloudflare One includes Browser Isolation. In contrast to legacy remote browser approaches, which send a slow and clunky version of the web page to the user, Cloudflare Browser Isolation draws an exact replica of the page on the user’s device, and then delivers that replica so quickly that it feels like a regular browser.
Cloud Access Security Broker (CASB)
A cloud access security broker scans, detects, and continuously monitors for security issues in SaaS applications. Organizations use CASB for:
Data security - e.g. ensuring a wrong file or folder is not shared publicly in Dropbox
User activity - e.g. alerting to suspicious user permissions changing in Workday at 2:00 AM
Misconfigurations - e.g. keeping Zoom recordings from becoming publicly accessible
Compliance - e.g. tracking and reporting who modified Bitbucket branch permissions
Shadow IT - e.g. detecting users that signed up for an unapproved application with their work email
API-driven CASBs leverage API integrations with various SaaS applications and take just a few minutes to connect. CASB can also be used in tandem with RBI to detect and then prevent unwanted behaviors to both approved and unsanctioned SaaS applications, like disabling the ability to download files or copy text out of documents. More on CASB here.
 Cloudflare One includes an API-driven CASB which gives comprehensive visibility and control over SaaS apps, so you can easily prevent data leaks and compliance violations.
Cloudflare One includes an API-driven CASB which gives comprehensive visibility and control over SaaS apps, so you can easily prevent data leaks and compliance violations.
Data Loss Prevention (DLP)
Data loss prevention tools detect and prevent data exfiltration (data moving without company authorization) or data destruction. Many DLP solutions analyze network traffic and internal "endpoint" devices to identify the leakage or loss of confidential information such as credit card numbers and personally identifiable information (PII). DLP uses a number of techniques to detect sensitive data including data fingerprinting, keyword matching, pattern matching, and file matching. More on DLP here.
 DLP capabilities for Cloudflare One are coming soon. These will include the ability to check data against common patterns like PII, label and index specific data you need to protect, and combine DLP rules with other Zero Trust policies.
DLP capabilities for Cloudflare One are coming soon. These will include the ability to check data against common patterns like PII, label and index specific data you need to protect, and combine DLP rules with other Zero Trust policies.
Firewall-as-a-service
Firewall-as-a-service, also referred to as cloud firewall, filters out potentially malicious traffic without requiring a physical hardware presence within a customer network. More on firewall-as-a-service here.
 Cloudflare One includes Magic Firewall, a firewall-as-a-service that allows you to filter any IP traffic from a single control plane and (new!) enforce IDS policies across your traffic.
Cloudflare One includes Magic Firewall, a firewall-as-a-service that allows you to filter any IP traffic from a single control plane and (new!) enforce IDS policies across your traffic.
Email security
Email security is the process of preventing email-based cyber attacks and unwanted communications. It spans protecting inboxes from takeover, protecting domains from spoofing, stopping phishing attacks, preventing fraud, blocking malware delivery, filtering spam, and using encryption to protect the contents of emails from unauthorized persons.
Email security tools can be used in conjunction with other secure access functions including DLP and RBI - for example, potentially suspicious links in emails can be launched in an isolated browser without blocking false positives. More on email security here.
 Cloudflare One includes Area 1 email security, which crawls the Internet to stop phishing, Business Email Compromise (BEC), and email supply chain attacks at the earliest stages of the attack cycle. Area 1 enhances built-in security from cloud email providers with deep integrations into Microsoft and Google environments and workflows.
Cloudflare One includes Area 1 email security, which crawls the Internet to stop phishing, Business Email Compromise (BEC), and email supply chain attacks at the earliest stages of the attack cycle. Area 1 enhances built-in security from cloud email providers with deep integrations into Microsoft and Google environments and workflows.
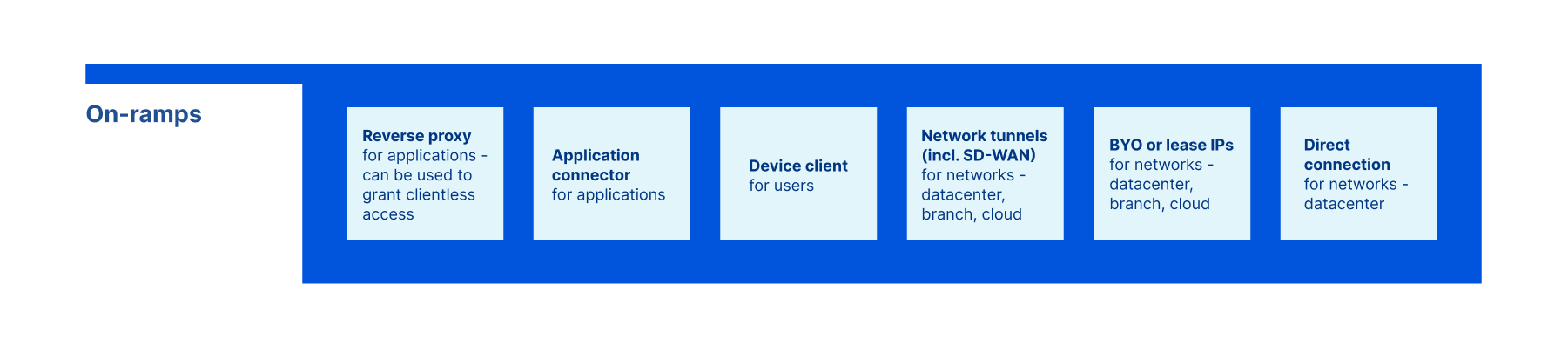
On-ramps: get connected
In order to apply secure access functions to your traffic, you need mechanisms to get that traffic from its source (whether that’s a remote user device, branch office, data center, or cloud) to the service edge (see below) where those functions operate. On-ramps are those mechanisms - the inputs and outputs in the IPO model, or in other words, the ways your traffic gets from point A to point B after filters have been applied.
Reverse proxy (for applications)
A reverse proxy sits in front of web servers and forwards client (e.g. web browser) requests to those web servers. Reverse proxies are typically implemented to help increase security, performance, and reliability. When used in conjunction with identity and endpoint security providers, a reverse proxy can be used to grant network access to web-based applications.
Cloudflare One includes one of the world’s most-used reverse proxies, which processes over 1.39 billion DNS requests every day.
Application connector (for applications)
For private or non-web-based applications, IT teams can install a lightweight daemon in their infrastructure and create an outbound-only connection to the service edge. These application connectors enable connectivity to HTTP web servers, SSH servers, remote desktops, and other applications/protocols without opening the applications to potential attacks.
Cloudflare One includes Cloudflare Tunnel. Users can install a lightweight daemon that creates an encrypted tunnel between their origin web server and Cloudflare’s nearest data center without opening any public inbound ports.
Device client (for users)
In order to get traffic from devices, including laptops and phones, to the service edge for filtering and private network access, users can install a client. This client, or “roaming agent,” acts as a forward proxy to direct some or all traffic from the device to the service edge.
Cloudflare One includes the WARP device client, which is used by millions of users worldwide and available for iOS, Android, ChromeOS, Mac, Linux, and Windows.
Bring-your-own or lease IPs (for branches, data centers, and clouds)
Depending on the capabilities of a SASE provider’s network/service edge, organizations may elect to bring their own IPs or lease IPs to enable entire network connectivity via BGP advertisement.
Cloudflare One includes BYOIP and leased IP options, both of which involve advertising ranges across our entire Anycast network.
Network tunnels (for branches, data centers, and clouds)
Most hardware or virtual hardware devices that sit at physical network perimeters are able to support one or multiple types of industry-standard tunneling mechanisms such as GRE and IPsec. These tunnels can be established to the service edge from branches, data centers and public clouds to enable network level connectivity.
Cloudflare One includes Anycast GRE and IPsec tunnel options, which are configured like traditional point-to-point tunnels but grant automatic connectivity to Cloudflare’s entire Anycast network for ease of management and redundancy. These options also enable easy connectivity from existing SD-WAN devices, which can enable simple to manage or entirely automated tunnel configuration.
Direct connection (for branches and data centers)
A final on-ramp option for networks with high reliability and capacity needs is to directly connect to the service edge, either with a physical cross-connect/last mile connection or a virtual interconnection through a virtual fabric provider.
Cloudflare One includes Cloudflare Network Interconnect (CNI), which enables you to connect with Cloudflare’s network via a direct physical connection or virtual connection through a partner. Cloudflare for Offices brings CNI directly to your physical premise for even simpler connectivity.
Service edge: the network that powers it all
Secure access functions need somewhere to operate. In the traditional perimeter architecture model, that place was a rack of hardware boxes in a corporate office or data center; with SASE, it’s a distributed network that is located as close as possible to users and applications wherever they are in the world. But not all service edges are created equal: for a SASE platform to deliver a good experience for your users, applications, and networks, the underlying network needs to be fast, intelligent, interoperable, programmable, and transparent. Let’s break down each of these platform capabilities in more detail.
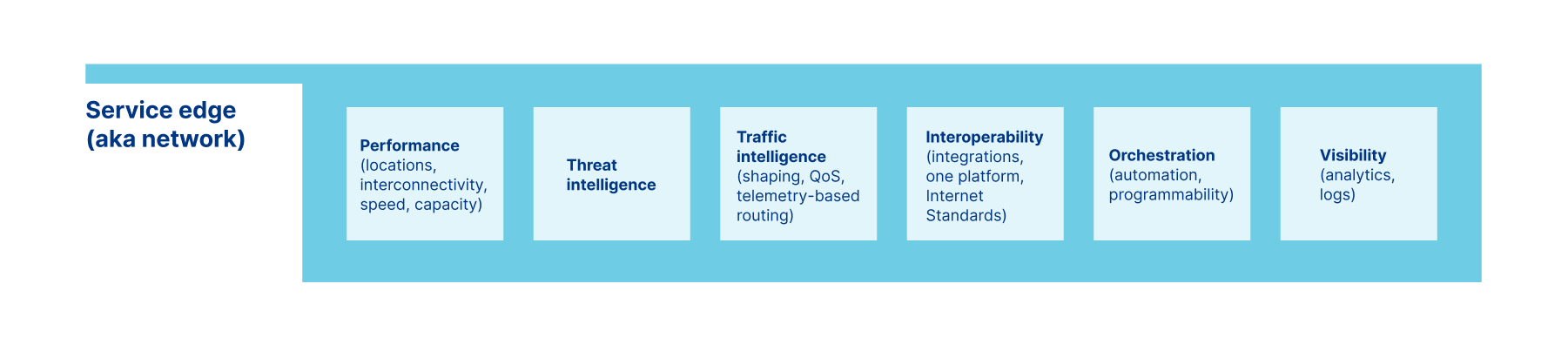
Performance: locations, interconnectivity, speed, capacity
Historically, IT teams have had to make tough trade off decisions between security and performance. These could include whether and which traffic to back haul to a central location for security filtering and which security functions to enable to balance throughput with processing overhead. With SASE, those trade-offs are no longer required, as long as the service edge is:
Geographically dispersed: it’s important to have service edge locations as close as possible to where your users and applications are, which increasingly means potentially anywhere in the world.
Interconnected: your service edge needs to be interconnected with other networks, including major transit, cloud, and SaaS providers, in order to deliver reliable and fast connectivity to the destinations you’re ultimately routing traffic to.
Fast: as expectations for user experience continue to rise, your service edge needs to keep up. Perceived application performance is influenced by many factors, from the availability of fast last-mile Internet connectivity to the impact of security filtering and encryption/decryption steps, so SASE providers need to take a holistic approach to measuring and improving network performance.
High capacity: with a SASE architecture model, you should never need to think about capacity planning for your security functions - “what size box to buy” is a question of the past. This means that your service edge needs to have enough capacity at each location where your network traffic can land, and the ability to intelligently load balance traffic to use that capacity efficiently across the service edge.
Cloudflare One is built on Cloudflare’s global network, which spans over 270 cities in over 100 countries, 10,500+ interconnected networks, and 140+ Tbps capacity.
Traffic intelligence: shaping, QoS, telemetry-based routing
On top of the inherent performance attributes of a network/service edge, it’s also important to be able to influence traffic based on characteristics of your individual network. Techniques like traffic shaping, quality of service (QoS), and telemetry-based routing can further improve performance for traffic across the security service edge by prioritizing bandwidth for critical applications and routing around congestion, latency, and other problems along intermediate paths.
Cloudflare One includes Argo Smart Routing, which optimizes Layer 3 through 7 traffic to intelligently route around congestion, packet loss, and other issues on the Internet. Additional traffic shaping and QoS capabilities are on the Cloudflare One roadmap.
Threat intelligence
In order to power the secure access functions, your service edge needs a continuously updating feed of intelligence that includes known and new attack types across all layers of the OSI stack. The ability to integrate third party threat feeds is a good start, but native threat intelligence from the traffic flowing across the service edge is even more powerful.
Cloudflare One includes threat intelligence gathered from the 20M+ Internet properties on Cloudflare’s network, which is continuously fed back into our secure access policies to keep customers protected from emerging threats.
Interoperability: integrations, standards, and composability
Your SASE platform will replace many of the components of your legacy network architecture, but you may choose to keep some of your existing tools and introduce new ones in the future. Your service edge needs to be compatible with your existing connectivity providers, hardware, and tools in order to enable a smooth migration to SASE.
At the same time, the service edge should also help you stay ahead of new technology and security standards like TLS 1.3 and HTTP3. It should also be fully composable, with every service working together to drive better outcomes than a stack of point solutions could alone.
Cloudflare One integrates with platforms like Identity Provider and Endpoint Protection solutions, SD-WAN appliances, interconnection providers, and Security Incident and Event Management tools (SIEMs). Existing security and IT tools can be used alongside Cloudflare One with minimal integration work.
Cloudflare is also a leader in advancing Internet and Networking standards. Any new web standard and protocols have likely been influenced by our research team.
Cloudflare One is also fully composable, allowing you to start with one use case and layer in additional functionality to create a “1+1=3” effect for your network.
Orchestration: automation and programmability
Deploying and managing your SASE configuration can be complex after scaling beyond a few users, applications, and locations. Your service edge should offer full automation and programmability, including the ability to manage your infrastructure as code with tools like Terraform.
Cloudflare One includes full API and Terraform support for easily deploying and managing configuration.
Visibility: analytics and logs
Your team should have full visibility into all the traffic routing through the service edge. In the classic perimeter security model, IT and security teams could get visibility by configuring network taps at the handful of locations where traffic entered and left the corporate network. As applications left the data center and users left the office, it became much more challenging to get access to this data. With a SASE architecture, because all of your traffic is routed through a service edge with a single control plane, you can get that visibility back - both via familiar formats like flow data and packet captures as well as rich logs and analytics.
All secure access components of Cloudflare One generate rich analytics and logs that can be evaluated directly in the Cloudflare One Dashboard or pushed in SIEM tools for advanced analytics.
Get started on your SASE journey with Cloudflare One
Over the next week, we will be announcing new features that further augment the capabilities of the Cloudflare One platform to make it even easier for your team to realize the vision of SASE. You can follow along at our Innovation Week homepage here or contact us to get started today.


