This post is also available in 简体中文, 繁體中文, 한국어, 日本語, Español, Bahasa Indonesia and ไทย.
Back in October 2020, we introduced Cloudflare One, our vision for the future of corporate networking and security. Since then, we’ve been laser-focused on delivering more pieces of this platform, and today we’re excited to announce two of its most foundational aspects: Magic WAN and Magic Firewall. Magic WAN provides secure, performant connectivity and routing for your entire corporate network, reducing cost and operational complexity. Magic Firewall integrates smoothly with Magic WAN, enabling you to enforce network firewall policies at the edge, across traffic from any entity within your network.
Traditional network architecture doesn’t solve today’s problems
Enterprise networks have historically adopted one of a few models, which were designed to enable secure information flow between offices and data centers, with access to the Internet locked down and managed at office perimeters. As applications moved to the cloud and employees moved out of offices, these designs stopped working, and band-aid solutions like VPN boxes don’t solve the core problems with enterprise network architecture.
On the connectivity side, full mesh MPLS (multiprotocol label switching) networks are expensive and time consuming to deploy, challenging to maintain, exponentially hard to scale, and often have major gaps in visibility. Other architectures require backhauling traffic through central locations before sending it back to the source, which introduces unacceptable latency penalties and necessitates purchasing costly hub hardware for maximum capacity rather than actual utilization. And most customers we’ve talked to are struggling with the worst of both worlds: a combination of impossible-to-manage architectures stitched together over years or decades. Security architects also struggle with these models - they have to juggle a stack of security hardware boxes from different vendors and trade off cost, performance, and security as their network grows.
Move your network perimeter to the edge and secure it as a service
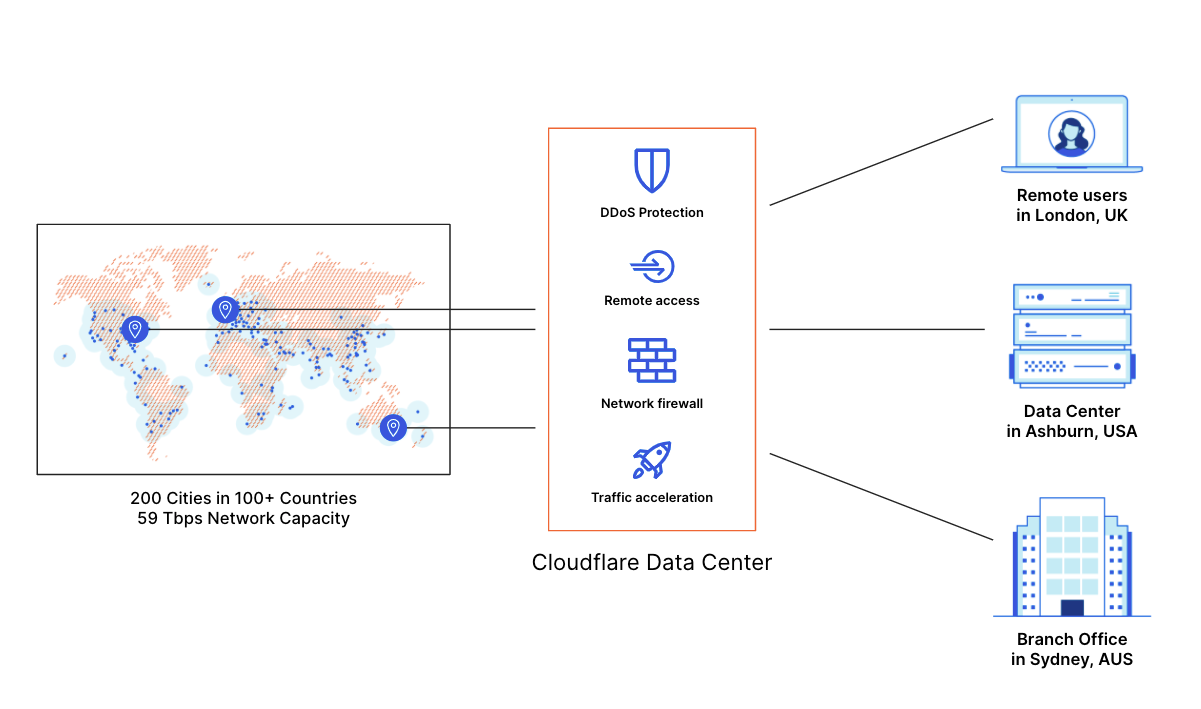
With Magic WAN, you can securely connect any traffic source - data centers, offices, devices, cloud properties - to Cloudflare’s network and configure routing policies to get the bits where they need to go, all within one SaaS solution. Magic WAN supports a variety of on-ramps including Anycast GRE tunnels, Cloudflare Network Interconnect, Argo Tunnel, WARP, and a variety of Network On-ramp Partners. No more MPLS expense or lead times, no more performance penalties from traffic trombones, and no more nightmare of managing a tangle of legacy solutions: instead, use Cloudflare’s global Anycast network as an extension of yours, and get better performance and visibility built-in.
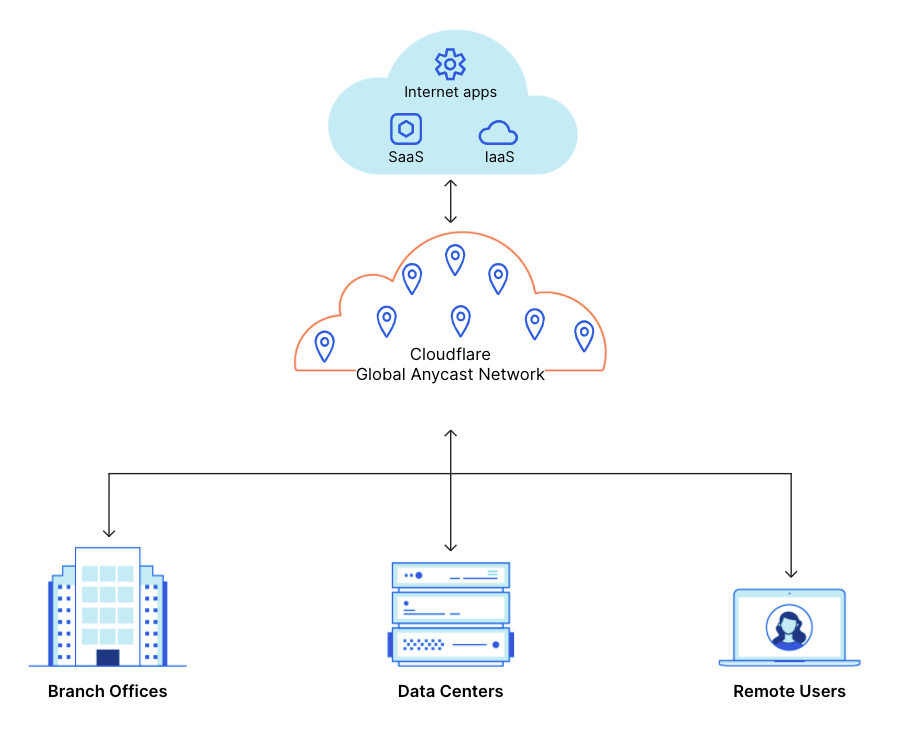
Once your traffic is connected to Cloudflare, how do you control which entities within your network are allowed to interact with each other, or the Internet? This is where Magic Firewall comes in. Magic Firewall allows you to centrally manage policy across your entire network, all at the edge as a service. Magic Firewall gives you fine-grained control over which data is allowed in and out of your network, or inside your network. Even better, you get visibility into exactly how traffic is flowing through your network from a single dashboard.
Magic WAN provides the foundation for the broad suite of functions included in Cloudflare One, which were all built in software from the ground up to scale and integrate smoothly. Magic Firewall is available for Magic WAN out of the box, and customers can easily activate additional Zero Trust security and performance features such as our Secure Web Gateway with remote browser isolation, Intrusion Detection System, Smart Routing, and more.
“Our network team is excited by Magic WAN. Cloudflare has built a global network-as-a-service platform that will help network teams manage complex edge and multi-cloud environments much more efficiently. Operating a single global WAN with built-in security and fast routing functionality — regardless of the HQ, data center, branch office, or end user location — is a game-changer in WAN technology.”
— Sander Petersson, Head of Infrastructure, FlightRadar24
What does this look like concretely? Let's explore some ways you can use Magic WAN and Magic Firewall to solve problems in enterprise networking and security with an example customer, Acme Corp.
Replace MPLS between branch offices & data centers
Today, Acme Corp has offices around the world that are each connected to regional data centers and to each other with MPLS. Each data center, which hosts corporate applications and a stack of hardware boxes to keep them secure, also has leased line connectivity to at least one other data center. Acme is also migrating some applications to the cloud, and they’re planning to establish direct connections from their data centers to cloud providers to boost security and reliability.
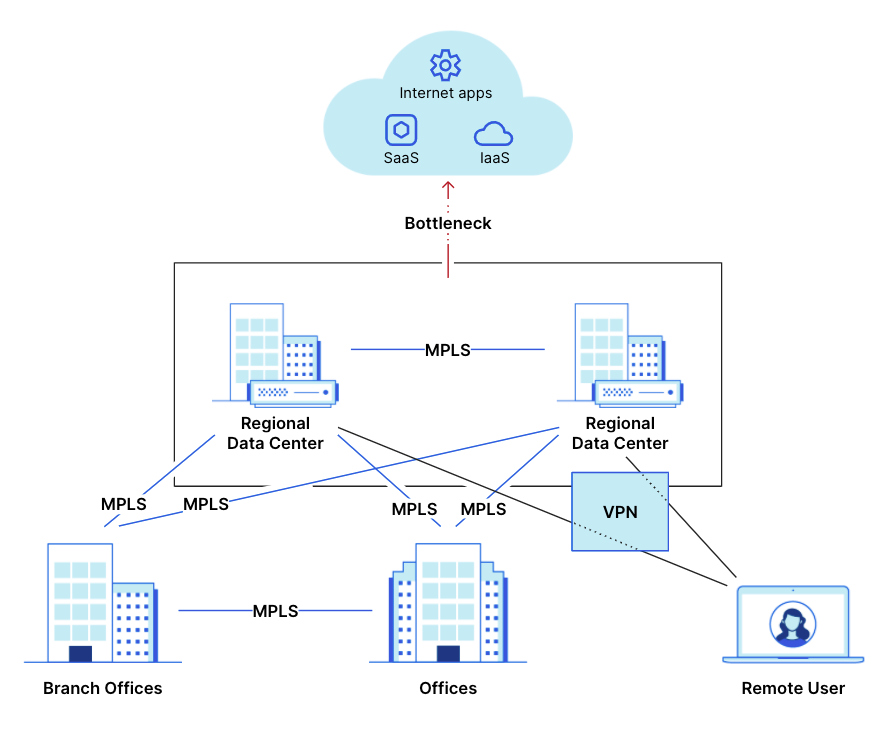
As Acme has grown, one of their network team's most consistent pain points is managing and maintaining their MPLS connectivity. It's expensive and deployment requires long lead times, limiting Acme’s speed of expanding into new locations (especially internationally) or supporting offices added through acquisitions. Employees in Acme’s offices connecting to cloud providers and SaaS apps experience frustrating latency, since traffic hairpins through an Acme data center for security policies enforced through a stack of hardware boxes before being sent to its destination. Traffic between offices, such as IP telephony and video conferencing, doesn’t have any security policies applied to it, presenting a gap in Acme’s security posture.
Just as they're working on transitioning to the cloud for compute and storage, Acme wants to migrate away from these private links and instead leverage the Internet, securely, for connectivity. They considered establishing fully meshed site-to-site IPSec VPN tunnels over the Internet, but the complexity strained their networking team as well as their heterogeneous router deployments. Magic WAN is ready to meet them where they are today, simplifying network management and delivering immediate performance benefits, as well as enabling Acme's gradual transition away from MPLS.
In this example deployment with Magic WAN, Acme connects each office and VPC to Cloudflare with Anycast GRE tunnels. With this architecture, Acme only needs to set up a single tunnel for each site/Internet connection in order to automatically receive connectivity to Cloudflare's entire global network (200+ cities in 100+ countries around the world) - like a hub and spoke architecture, except the hub is everywhere. Acme also chooses to establish dedicated private connectivity from their data centers with Cloudflare Network Interconnect, enabling even more secure and reliable traffic delivery and great connectivity to other networks/cloud providers through Cloudflare’s highly interconnected network.
Once these tunnels are established, Acme can configure allowed routes for traffic within their private network (RFC 1918 space), and Cloudflare gets the traffic where it needs to go, providing resiliency and traffic optimization. With an easy setup process that takes only a few hours, Acme Corp can start their migration away from MPLS. And as new Cloudflare One capabilities like QoS and Argo for Networks are introduced, Acme’s network performance and reliability will continue to improve.
Secure remote employee access to private networks
When Acme Corp's employees abruptly transitioned to working remotely last year due to the COVID-19 pandemic, Acme's IT organization scrambled to find short term fixes to maintain employee access to internal resources. Their legacy VPNs didn't hold up - Acme employees working from home struggled with connectivity, reliability, and performance issues as appliances were pushed beyond the limits they were designed for.
Thankfully, there's a better solution! Acme Corp can use Cloudflare for Teams and Magic WAN to provide a secure way for employees to access resources behind private networks from their devices, wherever they're working. Acme employees install the WARP client on their devices to send traffic to Cloudflare's network, where it can be authenticated and routed to private resources in data centers or VPCs that are connected to Cloudflare via GRE tunnel (shown in the previous example), Argo Tunnel, Cloudflare Network Interconnect, or IPSec (coming soon). This architecture solves the performance and capacity issues Acme experienced with their legacy VPNs - rather than sending all traffic through single choke point devices, it’s routed to the closest Cloudflare location where policy is applied at the edge before being sent along an optimized path to its destination.
Traffic from Acme Corp's employee devices, data centers and offices will also be able to be policed by Magic Firewall for powerful, granular policy control that's enforced across all "on-ramps." Whether employees are connecting from their phones and laptops or working from Acme offices, the same policies can be applied in the same place. This simplifies configuration and improves visibility for Acme's IT and security teams, who will be able to log into the Cloudflare dashboard to see and control policies in one place - a game changer compared to managing employee access across different VPNs, firewalls, and cloud services.
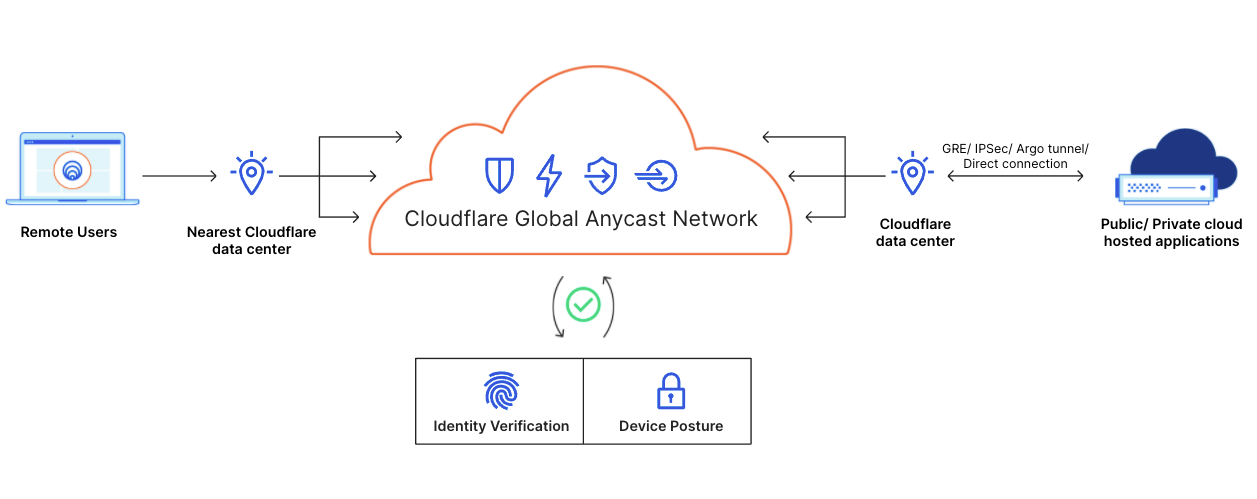
This solution allows Acme to transition away from their VPN, firewall, and secure web gateway appliances, improving performance and enabling easy policy management across traffic from wherever their employees are working.
Migrate network and security functions to the edge
Historically, Acme relied on stacks of hardware appliances in physical offices and data centers to enforce network security and get visibility into what’s happening on the network: specialized firewalls to inspect inbound or outbound traffic, intrusion detection systems and SIEMs. As their organization is moving to the cloud and rethinking the future of remote work, the Acme security team is looking for sustainable solutions that improve security, even beyond what used to be possible in their traditional castle-and-moat architecture.
Previously, we walked through how Acme could configure Magic WAN to send traffic from offices, data centers, cloud properties, and devices to Cloudflare’s network. Once this traffic is flowing through Cloudflare, it’s easy to add access controls and filtering functions to augment or replace on-prem security hardware, all delivered and administered through a single pane of glass.
With Magic Firewall, customers get a single firewall-as-a-service that runs at the edge, replacing clunky boxes they have installed at branch offices or data centers. Magic Firewall allows them to easily manage configuration, but also simplifies compliance auditing.
To control access, customers can put policies in place that determine exactly which traffic is allowed to go where. For example, Acme wants traffic to flow from the Internet to their web servers inside data centers on port 80 and 443, but wants to lock down SSH access to only certain private networks inside branch offices.
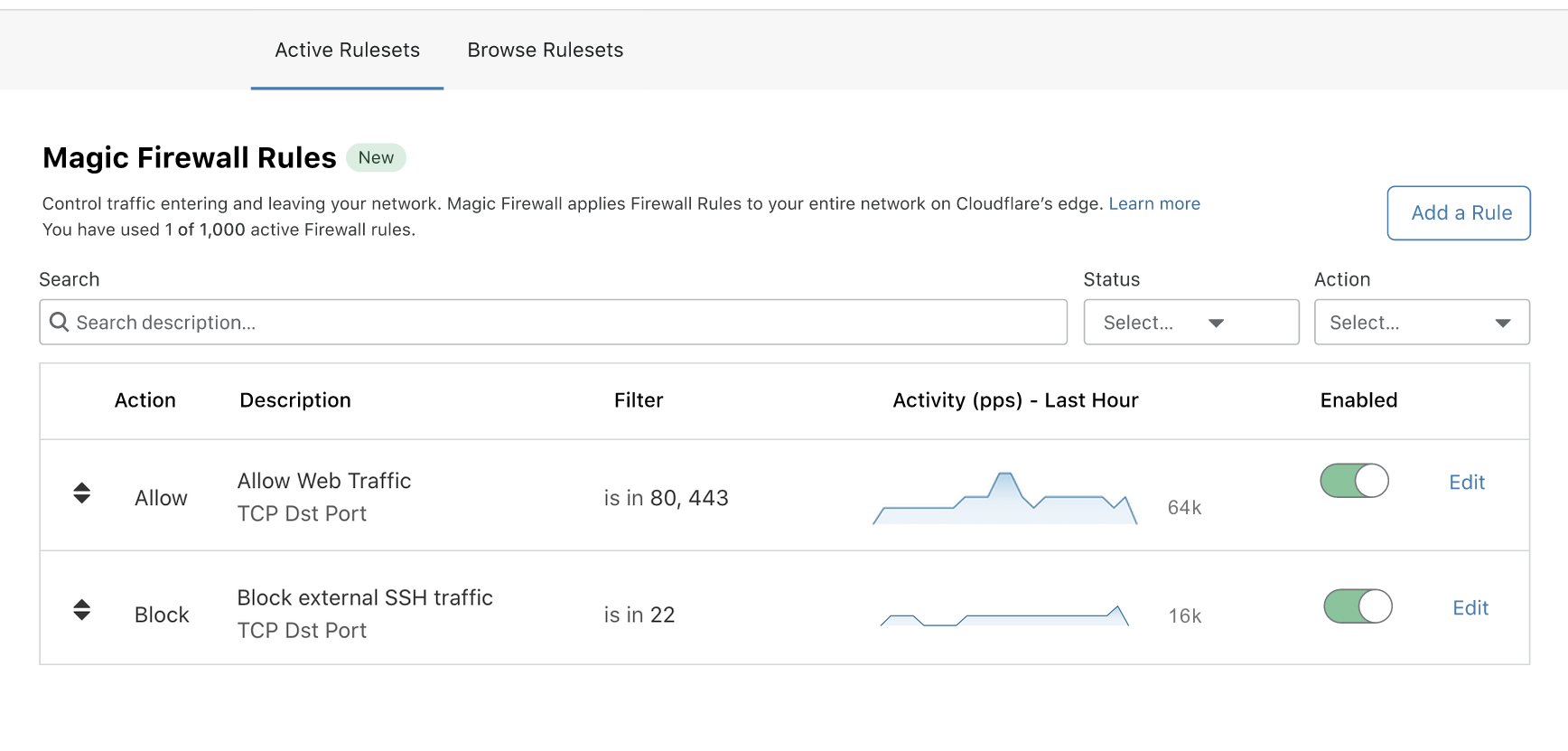
If Acme wants to go further in locking down their network, they can adopt a Zero Trust access model with Access and Gateway to control who can reach what, and how, across all their traffic flowing through the Cloudflare network. As Cloudflare releases new filtering and control functions, like our upcoming IDS/IPS and DLP solutions, Acme can enable them to further increase security with only a few clicks.
Acme’s long-term goal is to transition all security and performance functions to the cloud, consumed as a service. Magic WAN enables a smooth path for this migration, allowing them to gradually deepen their security posture as they retire legacy hardware.
Increased cloud adoption along with the recent pivot to remote workers has increased the volume of Internet, SaaS, and IaaS traffic straining traditional network architectures such as MPLS. WAN architectures that offer a global scale, integrated enterprise network security functions, and direct, secure connectivity to remote users are key to organizations looking to increase their operational agility and lower total costs of ownership.
— Ghassan Abdo, IDC Research VP, WW Telecom, Virtualization & CDN
Cloudflare’s network as an extension of yours
Like many of our products, Cloudflare One started as a collection of solutions to problems that we experienced in growing and securing our own network. Magic WAN and Magic Firewall allow us to extend the benefits of our careful architecture decisions over the past ten years to customers:
- Global scale & close to eyeballs: wherever your offices, data centers, and users are, we’re close by. We’ve worked hard to establish great connectivity to eyeball networks because of our CDN business, which pays dividends for remote workers who need great connectivity from their homes back to your network. It also means we can stop threats at the edge, close to their source, rather than running the risk of malicious traffic overwhelming capacity-limited on prem appliances.
- Hardware and carrier-agnostic: use whatever hardware you have today to connect to us, and get the benefits of resiliency afforded by our diverse carrier connectivity.
- Built from scratch to work together: we’ve developed our products in software, from the ground up, to integrate easily. We think constantly about how our products can integrate to make each other better as they’re created and evolved.
Get started today
Magic WAN is available in limited beta, and Magic Firewall is generally available for all Magic Transit customers and included out of the box with Magic WAN. If you’re interested in testing out Magic WAN or want to learn more about how Cloudflare can help your organization replace legacy MPLS architecture, secure access for remote workers, and deepen your security posture while reducing total cost of ownership, please get in touch.

