When Cloudflare first launched in 2010, network security still relied heavily on physical security. To connect to a private network, most users simply needed to be inside the walls of the office. Once on that network, users could connect to corporate applications and infrastructure.
When users left the office, a Virtual Private Network (VPN) became a bandaid to let users connect back into that office network. Administrators poked holes in their firewall that allowed traffic to route back through headquarters. The backhaul degraded user experience and organizations had no visibility into patterns and events that occurred once users were on the network.
Cloudflare Access launched two years ago to replace that model with an identity-based solution built on Cloudflare’s global network. Instead of a private network, teams secure applications with Cloudflare’s network. Cloudflare checks every request to those applications for identity, rather than IP ranges, and accelerates those connections using the same network that powers some of the world’s largest web properties.
In this zero-trust model, Cloudflare Access checks identity on every request - not just the initial login to a VPN client. Administrators build rules that Cloudflare’s network continuously enforces. Each request is evaluated for permission and logged for audit purposes. However, users can take their passwords and 2FA keys to unapproved devices. Logins from unmanaged devices, like a personal iPad, can violate an organization’s compliance audit. Users can also connect from corporate devices that are infected with malware, posing a risk that it could spread further.
Instead of the walls of an office building, modern physical security relies on organizations that control which devices can, and cannot, connect to corporate resources. The identity of the device can be evaluated alongside the identity of the user to keep data and applications safer.
Starting today, Cloudflare for Teams customers can add that layer of device security into their deployment with Tanium’s endpoint management platform. Cloudflare and Tanium are partnering to make zero-trust security seamless, combining Cloudflare’s network with Tanium’s on-device security.
Cloudflare Access
Cloudflare Access secures applications by applying zero-trust enforcement to every request. Rather than trusting any users on a private network who logged into a VPN client, Access checks for identity any time someone attempts to reach the application. With Cloudflare’s global network, that check takes place in a data center in over 200 cities around the world to avoid compromising performance.
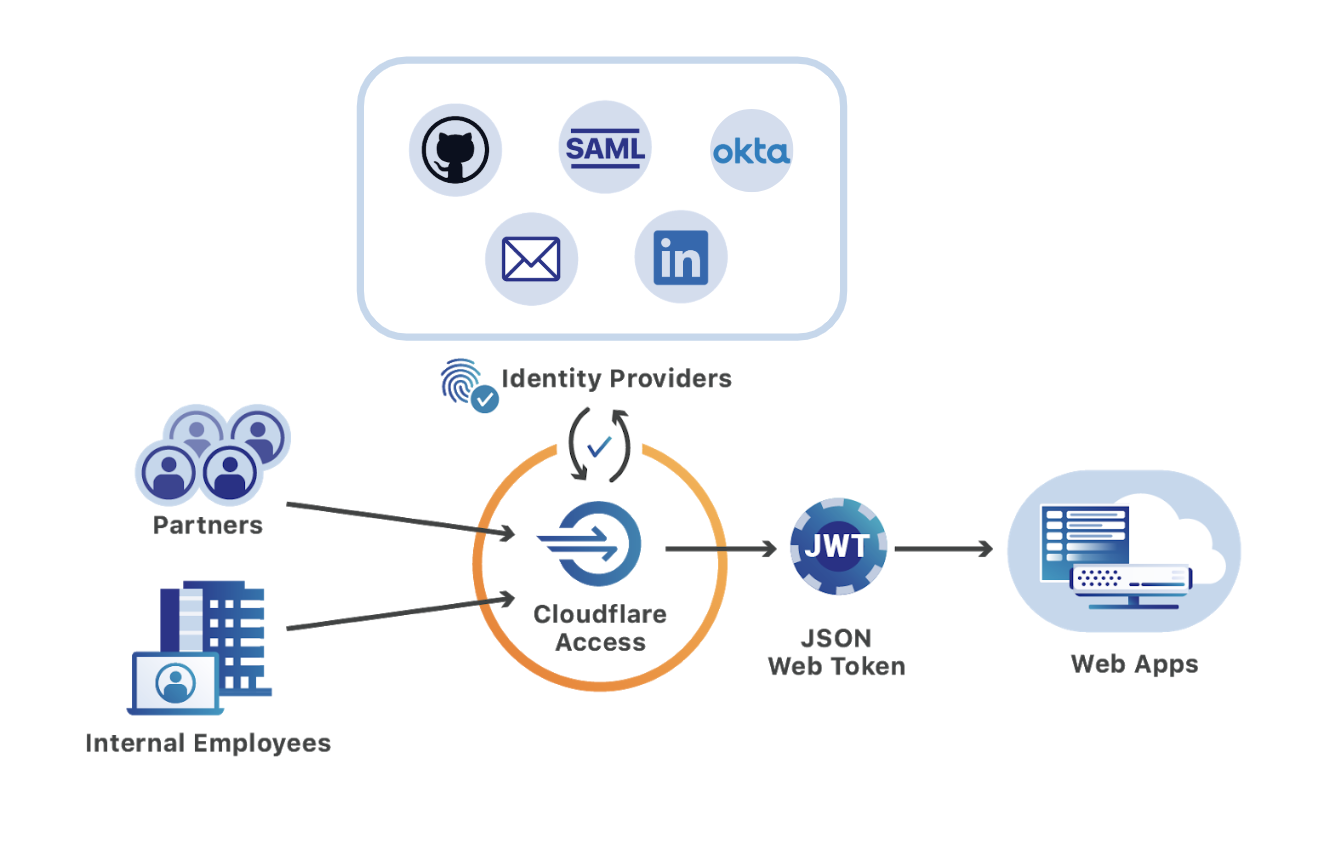
Behind the scenes, administrators build rules to decide who should be able to reach the tools protected by Access. In turn, when users need to connect to those tools, they are prompted to authenticate with one of the identity provider options. Cloudflare Access checks their login against the list of allowed users and, if permitted, allows the request to proceed.
Prior to this announcement, the rules that administrators could create relied entirely on a user login. Today, Cloudflare and Tanium customers can ensure any connection to their corporate resources is protected with two layers of assurance; number one, the user’s corporate credentials, and number two, their managed device.
Adding Tanium’s endpoint security
Tanium delivers a unified platform that consists of agents running on corporate devices that constantly evaluate and monitor the health of the endpoint. The solution reduces IT and Security complexity by providing comprehensive visibility and control over all endpoints in a single platform. 50% of the Fortune 100 and 4 of 5 U.S. military branches rely on Tanium to manage and secure devices, wherever they operate.
Tanium deployments use a single agent to replace several legacy approaches to endpoint management and security. For IT teams, the agent provides inventory management, device configuration, and performance monitoring to reduce the burden of managing fleets of endpoints. Security teams can use that same agent for detection and response, patch updates, and data risk and privacy enforcement.
Like Cloudflare’s products for network performance and security, Tanium replaces traditional endpoint solutions with a single platform to keep devices safe. Starting today, organizations can connect both platforms for end-to-end network and endpoint security.
How it works
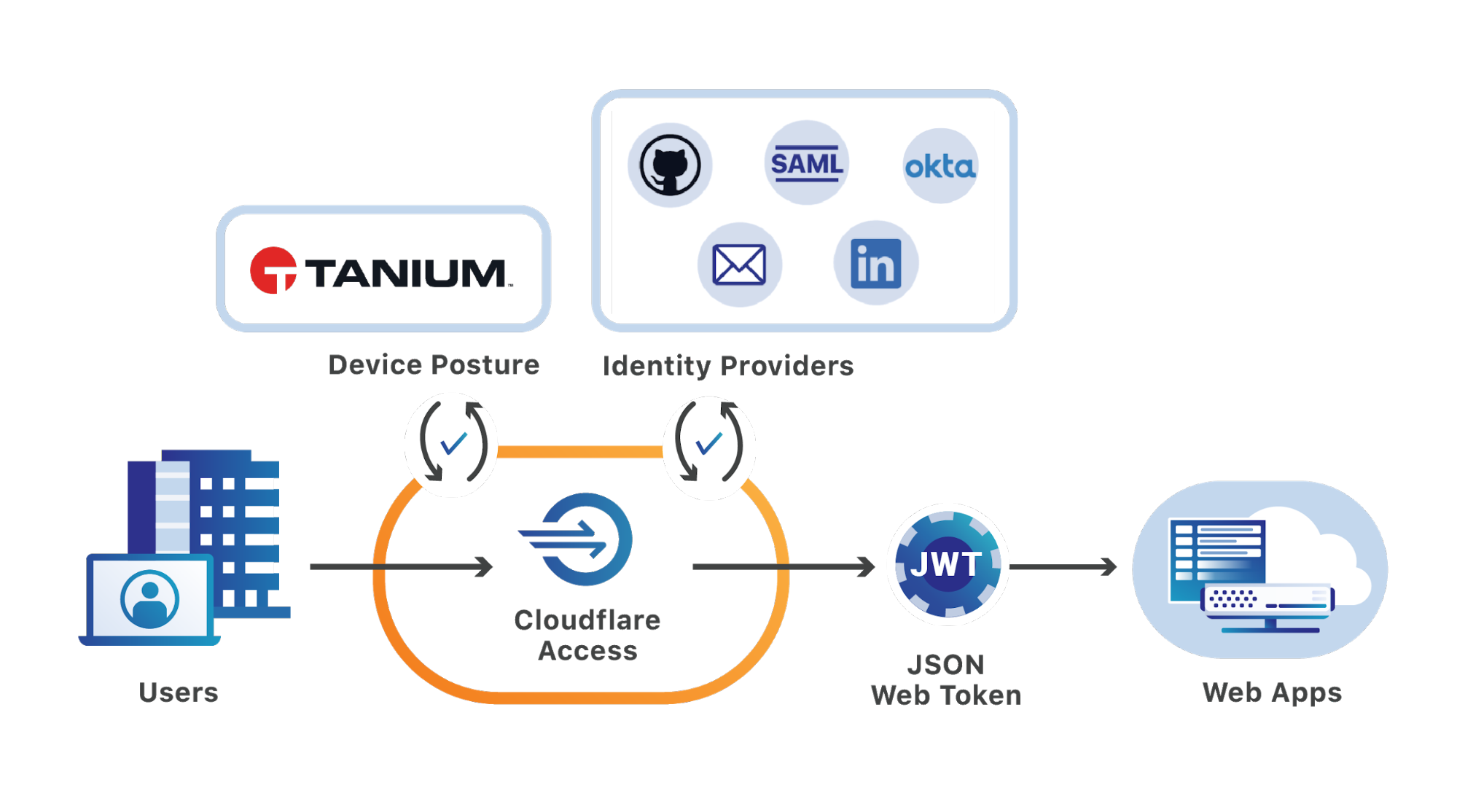
Integrating Tanium and Cloudflare for Teams takes 10 minutes. Once configured, administrators can build rules that require users connecting to applications to both login with their SSO and use a device managed by Tanium.
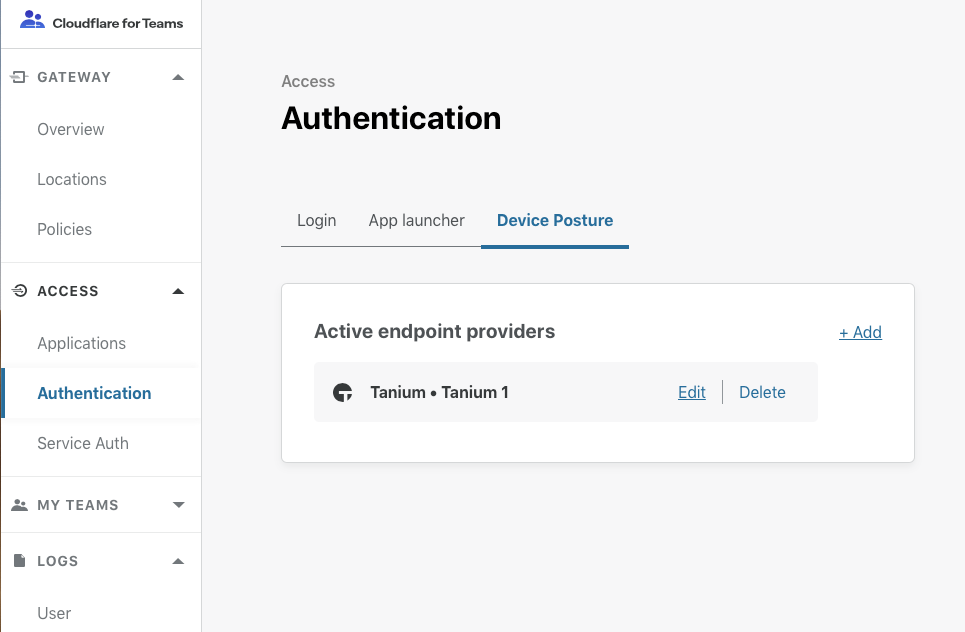
In the new Cloudflare for Teams UI, administrators can add Tanium as an authentication mechanism. The UI will prompt them to add their Tanium public certificate and the endpoint used to validate the connecting device. With that information, Cloudflare Access can query the device’s health when evaluating a connection without the risk that the device could be impersonated.
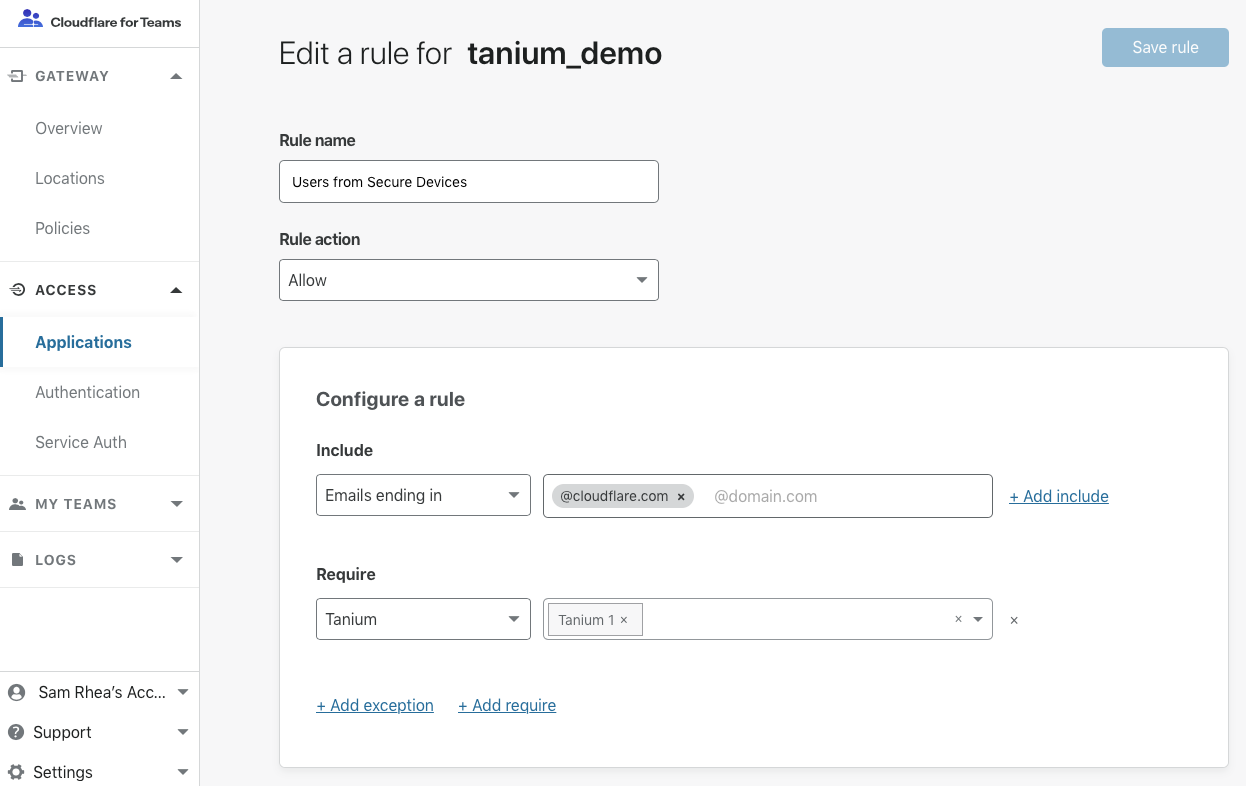
Administrators can then copy their Cloudflare for Teams public certificate and add it into their Tanium deployment. With that certificate, Tanium administrators can ensure that the only service that can query for data from the endpoint is their unique Cloudflare for Teams account.
Finally, administrators can add new rules into their Cloudflare Access policies that evaluate device posture. When users connect to resources secured by Access, Cloudflare’s network will check that the user authenticates with their identity provider and is connecting from a healthy, Tanium-monitored, device.
Cloudflare’s network and Tanium’s distribution makes that check seamless for the end user. Cloudflare Access runs in all of Cloudflare’s data centers in 200 cities around the world; putting enforcement decisions within 100ms of 99% of the world’s Internet connected population. By integrating directly with the Tanium agent, the evaluation can also occur without a connection back to the Tanium administrative layer.
What’s next?
With this integration, organizations can get defense in depth for corporate apps with Tanium and Access working together to secure user connections. All Cloudflare for Teams customers who have a Tanium deployment can begin integrating device posture into their Access policies today at no additional cost.
If you’re interested in taking advantage of this integration, we’re standing by to help you set it up. Fill out the form here and a member of our team will get in touch to help answer any questions.
If you already use Tanium or Cloudflare Access and want to try it out yourself, documentation from Cloudflare for Teams and Tanium is available to get started today.

