What is secondary DNS?
In a traditional sense, secondary DNS servers act as a backup to the primary authoritative DNS server. When a change is made to the records on the primary server, a zone transfer occurs, synchronizing the secondary DNS servers with the primary server. The secondary servers can then serve the records as if they were the primary server, however changes can only be made by the primary server, not the secondary servers. This creates redundancy across many different servers that can be distributed as necessary.
There are many common ways to take advantage of Secondary DNS, some of which are:
- Secondary DNS as passive backup - The secondary DNS server sits idle until the primary server goes down, at which point a failover can occur and the secondary can start serving records.
- Secondary DNS as active backup - The secondary DNS server works alongside the primary server to serve records.
- Secondary DNS with a hidden primary - The nameserver records at the registrar point towards the secondary servers only, essentially treating them as the primary nameservers.
What is secondary DNS Override?
Secondary DNS Override builds on the Secondary DNS with a hidden primary model by allowing our customers to not only serve records as they tell us to, but also enable them to proxy any A/AAAA/CNAME records through Cloudflare's network. This is similar to how Cloudflare as a primary DNS provider currently works.
Consider the following example:
example.com Cloudflare IP - 192.0.2.0
example.com origin IP - 203.0.113.0
In order to take advantage of Cloudflare's security and performance services, we need to make sure that the origin IP stays hidden from the Internet.
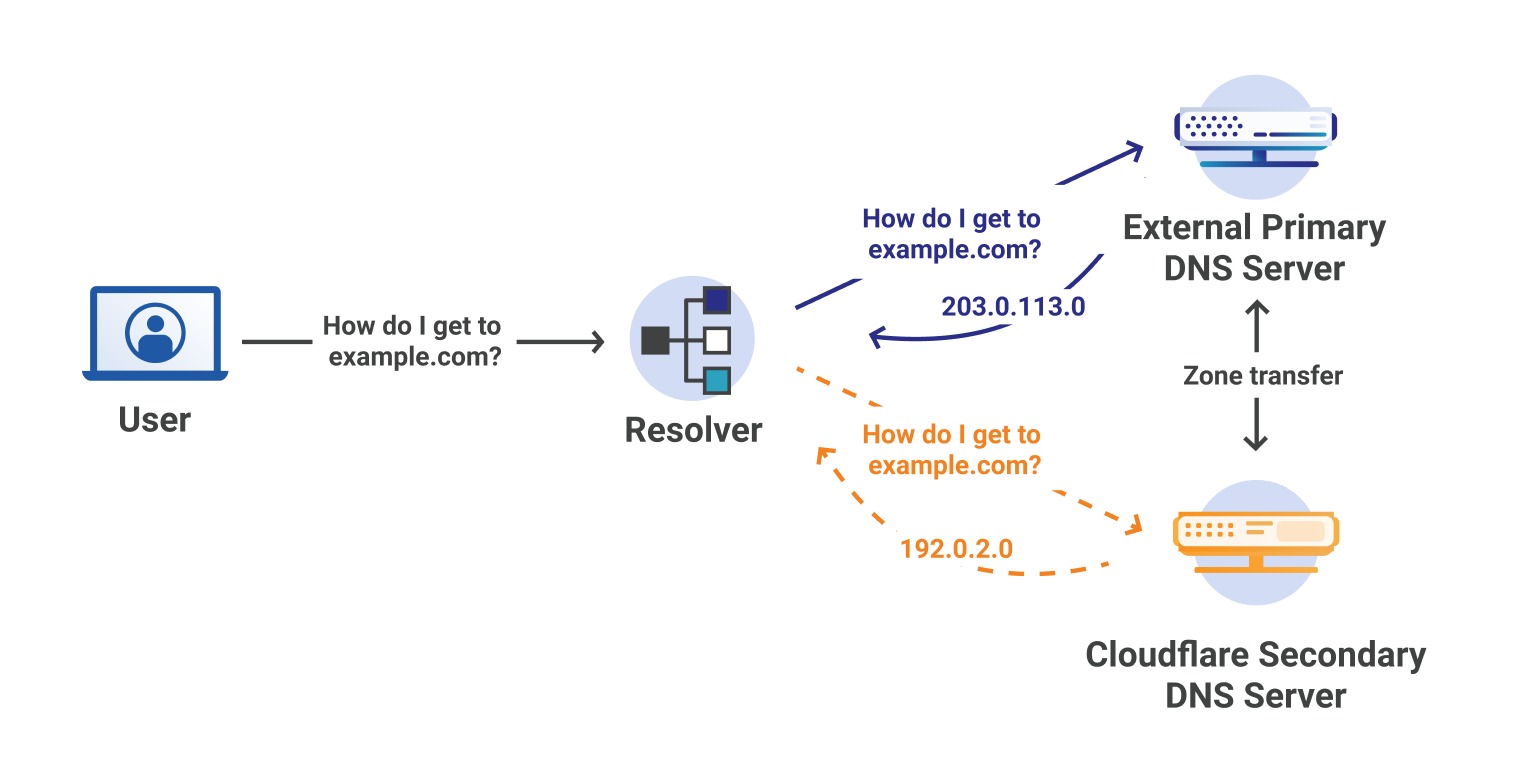
Figure 1 shows that without a hidden primary nameserver, the resolver can choose to query either one. This opens up two issues:
- Violates RFC 1034 and RFC 2182 because the Cloudflare server will be responding differently than the primary nameserver.
- The origin IP will be exposed to the Internet.
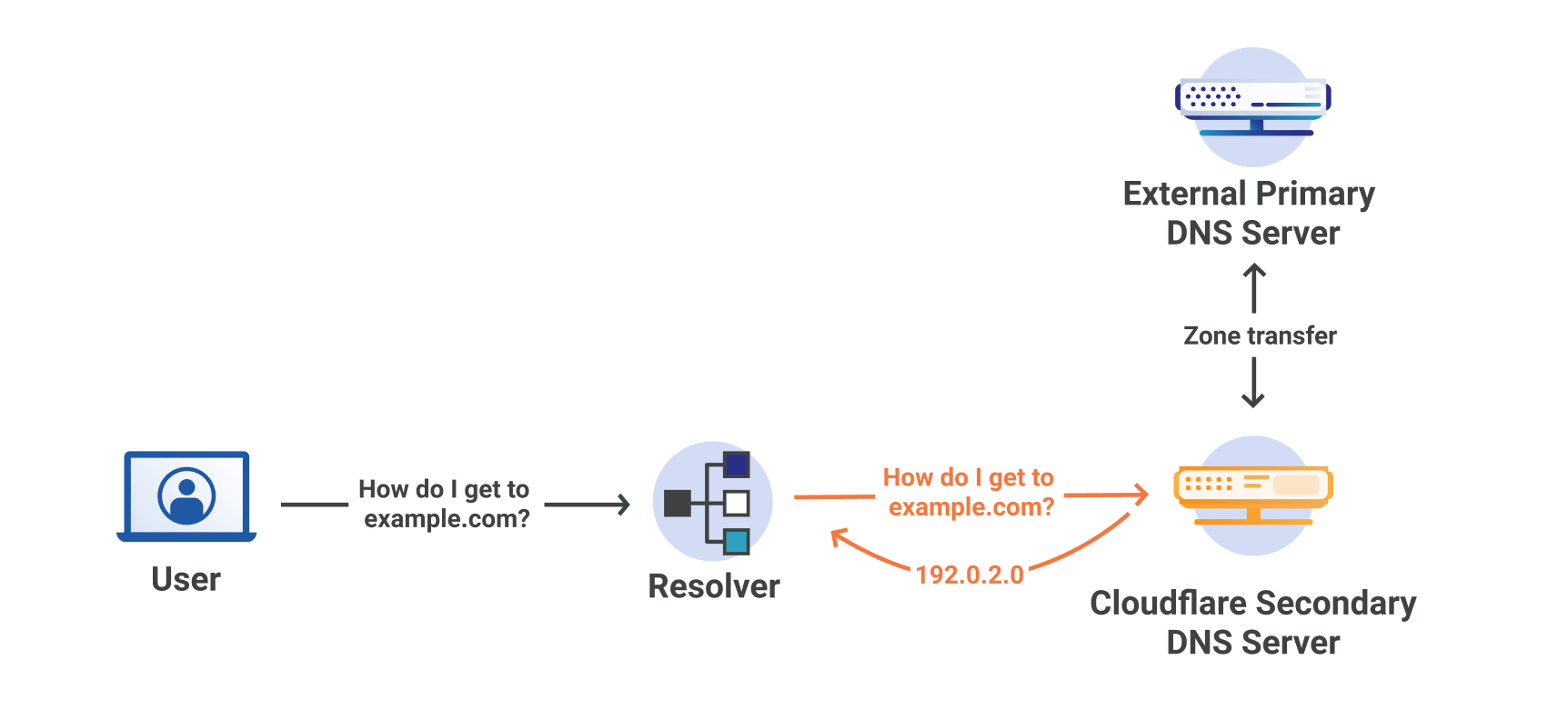
Figure 2 shows the resolver always querying the Cloudflare Secondary DNS server.
How Does Secondary DNS Override work
The Secondary DNS Override UI looks similar to the primary UI, the only difference is that records cannot be edited.
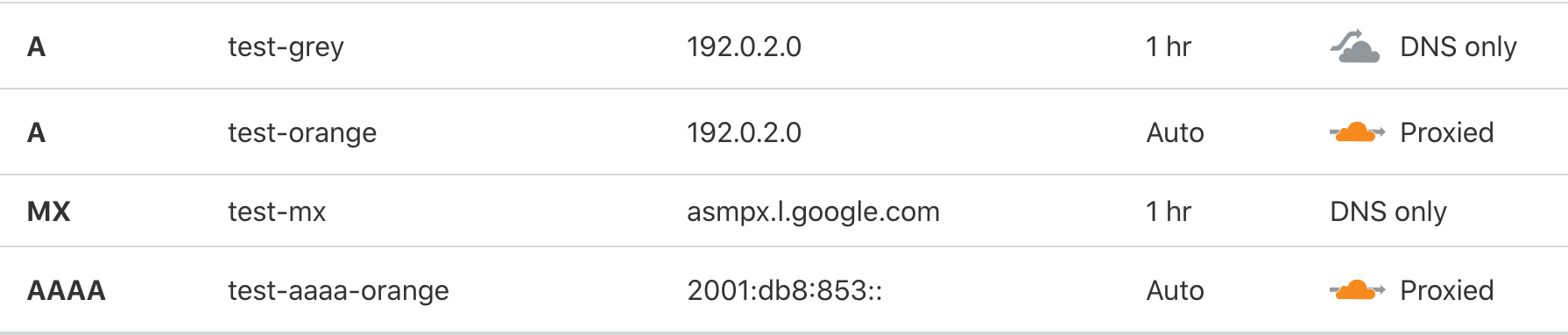
In figure 3, all of the records have been transferred from the primary DNS server. test-orange and test-aaaa-orange have been overridden to proxy through the cloudflare network, while test-grey and test-mx are treated as regular DNS records.
Behind the scenes we store override records that pair with transferred records based on the name. For secondary override we don’t care about the type when overriding records, because of two things:
- According to RFC 1912 you cannot have a CNAME record with the same name as any other record. (This does not apply to some DNSSEC records, see RFC 2181)
- A and AAAA records are both address type records which should be either all proxied or all not proxied under the same name.
This means if you have several A and several AAAA records all with the name “example.com”, if one of them is proxied, all of them will be proxied. The UI helps abstract the idea that we are storing additional override records through the “orange cloud” button, which when clicked, will create an override record which applies to all A/AAAA or CNAME records with that name.
CNAME at the Apex
Normally, putting a CNAME at the apex of a zone is not allowed. For example:
example.com CNAME other-domain.com
Is not allowed because this means that there will be at least one other SOA record and one other NS record with the same name, disobeying RFC 1912 as mentioned above. Cloudflare can overcome this through the use of CNAME Flattening, which is a common technique used within the primary DNS product today. CNAME flattening allows us to return address records instead of the CNAME record when a query comes into our authoritative server.
Contrary to what was said above regarding the prevention of editing records through the Secondary DNS Override UI, the CNAME at the apex is the one exception to this rule. Users are able to create a CNAME at the apex in addition to the regular secondary DNS records, however the same rules defined in RFC 1912 also apply here. What this means is that the CNAME at the apex record can be treated as a regular DNS record or a proxied record, depending on what the user decides. Regardless of the proxy status of the CNAME at the apex record, it will override any other A/AAAA records that have been transferred from the primary DNS server.
Merging Secondary, Override and CNAME at Apex Records
At record edit time we do all of the merging of the secondary, override and CNAME at the apex records. This means that when a DNS request comes in to our authoritative server at the edge, we can still return the records in blazing fast times. The workflow is shown in figure 4.
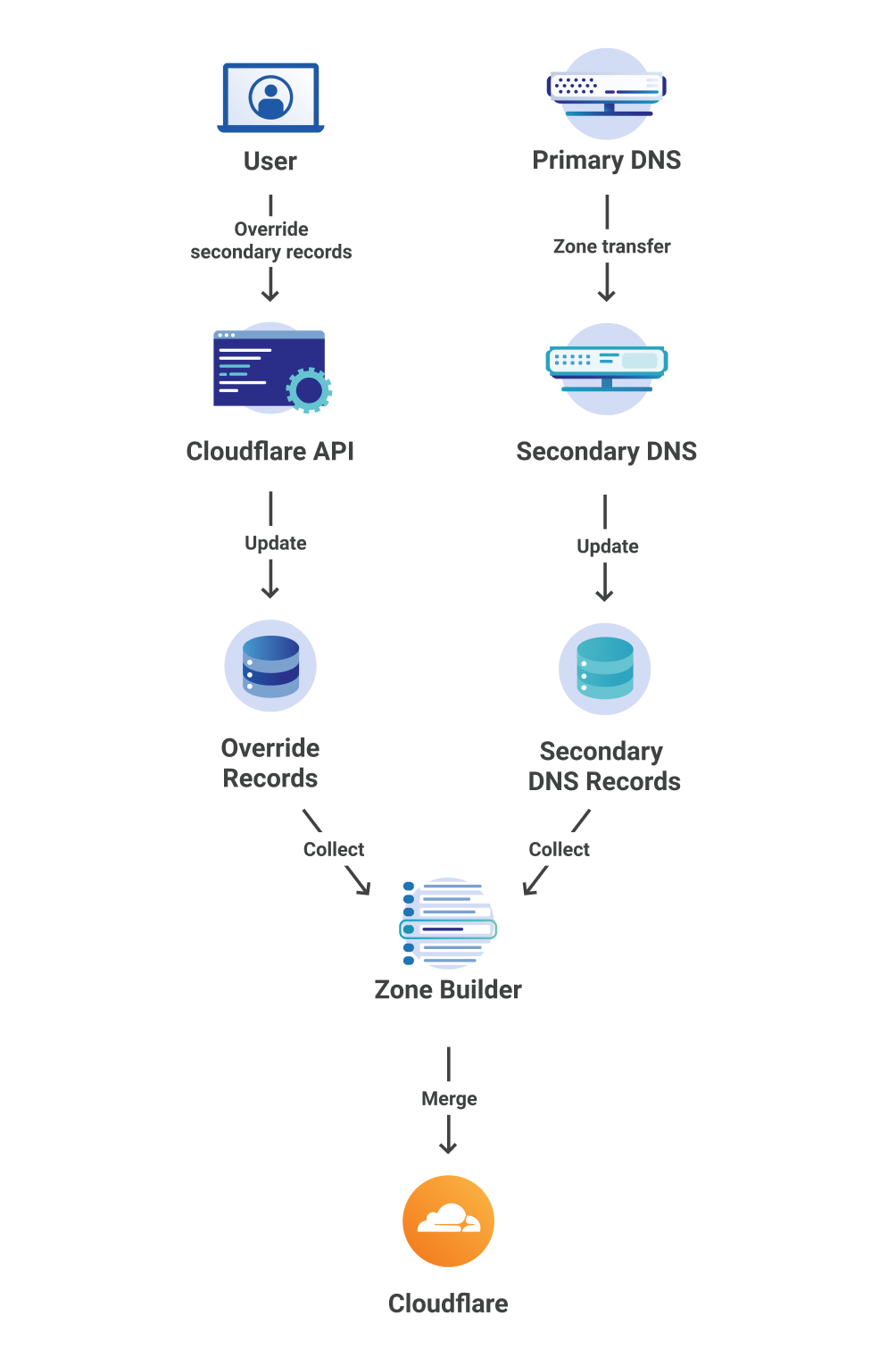
Within the zone builder the steps are as follows:
- Check if there is any CNAME at the apex, if so, override all other A/AAAA secondary records at the apex.
- For each secondary record, check if there is a matching override record, if so, apply the proxy status of the override record to all secondary records with that name.
- Leave all other secondary records as is.
Getting Started
Secondary DNS Override is a great option for any users that want to take advantage of the Cloudflare network, without transferring all of their zones to Cloudflare DNS as a primary provider. Security and access control can be managed on the primary side, without worrying about unauthorized edits of information on the Cloudflare side.
Secondary DNS Override is currently available on the Enterprise plan, if you’d like to take advantage of it, please let your account team know. For additional documentation on Secondary DNS Override, please refer to our support article.

