One of the many great features that CloudFlare provides is protection from Distributed Denial of Service (DDoS) attacks. A malicious party who wants to make your website or web service unavailable could try to overwhelm it with requests from compromised machines (or bots) all around the world. With a large enough volume of requests, your server may become overloaded and not be able to provide its services to legitimate clients. This is the typical scenario in a denial of service attack.
The attacking machines use the public domain name service (DNS) to look up the IP address that hosts your domain (www.sample.com) and send their traffic to that machine hoping to shut it down.
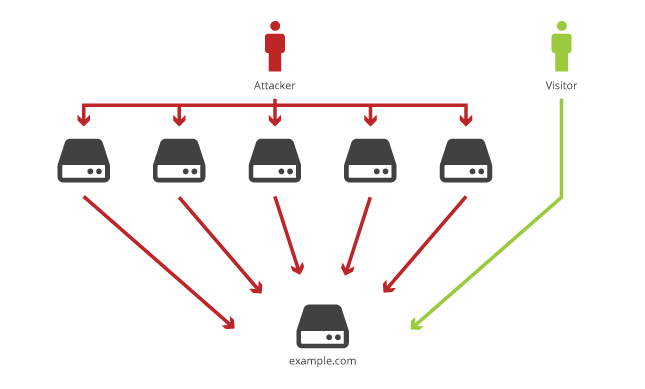
Signing up for CloudFlare is like taking your number out of the phone book, and putting in CloudFlare’s number under your name. When someone attempts to look up who hosts your domain, DNS will return an IP address in the CloudFlare network. If an attacker tries to take down your site, their traffic will go to CloudFlare machines around the world instead of directly to your web server. The CloudFlare network acts as a filter to block bad traffic and only send legitimate traffic through to your origin server.
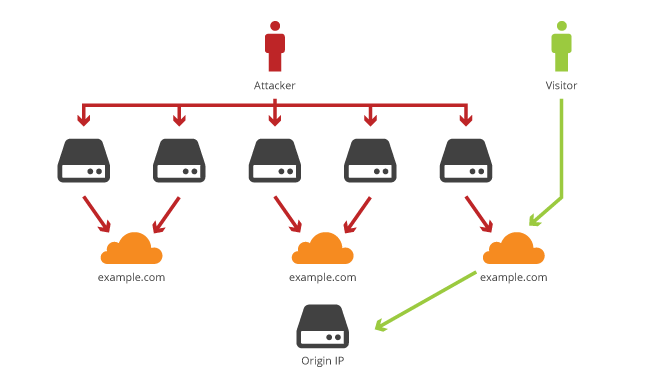
Just as removing your phone number from the phone book won't stop telemarketers from calling it, enabling CloudFlare doesn't stop clever attackers who know your IP address from sending traffic to it directly. Just because your origin server's IP address is no longer advertised over DNS, it's still connected to the internet. If your IP address is not kept secret, attackers can bypass the CloudFlare network and attack your servers directly.
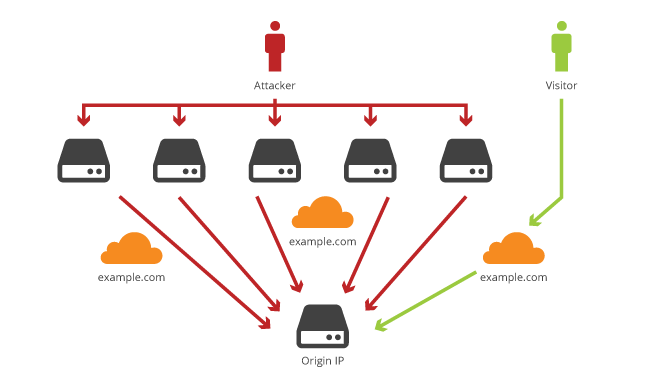
Here are some helpful tips to help keep your origin IP secure to protect against clever attackers who want to bypass CloudFlare’s DDoS protection:
Keep all subdomains on CloudFlare
When you sign up for CloudFlare, CloudFlare automatically adds a 'direct' subdomain. The 'direct' subdomain does not get the benefit of the CloudFlare proxy service by default. For maximum security, you should rename the 'direct' subdomain to something that can't be guessed easily or remove it altogether. Otherwise, an attacker can use the subdomain to look up your origin IP address. If you receive email for the domain signed up with CloudFlare use a separate server for mail; if not the MX record would reveal the IP address of your server.
Wildcard subdomains
CloudFlare powers DNS for wildcard subdomains, but only offers the performance and security proxy service for wildcard subdomains at the Enterprise level. As a result, if you are a Free, Pro or Business customer, wildcard subdomain records can not be proxied through CloudFlare and should be removed for DDoS protection. Otherwise, an attacker could use the wildcard subdomains to look up your origin IP.
Review DNS records
None of the DNS records should contain any mention of the origin IP. Take a close look at any SPF and TXT records to make sure they do not contain any information about the origin.
Don't host mail or other services on the same server as your web server
If your mail server hosted by the same IP as your http server, an attacker could find the IP address from an outgoing email. For example, an attacker could send an email to a non-existent email address on your server causing a bounce; the bounce might contain the IP address of your server in its headers.
Never initiate an outbound connection based on user action
If the attacker can get your web server to connect to an arbitrary address, they will reveal your origin IP. Features like "upload from URL" that allow the user to upload a photo from a given URL should be configured so that the server doing the download is not the website origin server. This is important because if an attacker can choose the URL entered, they can set up a web site specifically to monitor who connects to it, or use a public service that monitors the IPs that contact unique URLs.
Information disclosure vulnerabilities
Make sure that your web server and web application are patched against all known information disclosure vulnerabilities.
Change your origin IP once configured for maximum DDoS protection on CloudFlare
DNS records are public domain and there are many places where historical records are archived. These historical DNS records will contain your original IP from before signing up with CloudFlare. If you are a target, the attacker probably already has your previous DNS record.
Additional security resources
If you are concerned about security, review these two documents that outline advanced security steps for CloudFlare users.
Security is tough. Attackers only need to find one flaw or weakness in order to do a lot of damage. Following these steps will help keep your origin IP address private and help CloudFlare prevent DDoS attacks against your site.

