This post is also available in 简体中文, 繁體中文, 日本語, 한국어, Deutsch, Français, Español and Italiano.
Today, we are very excited to announce multiple new integrations with CrowdStrike. These integrations combine the power of Cloudflare’s expansive network and Zero Trust suite, with CrowdStrike’s Endpoint Detection and Response (EDR) and incident remediation offerings.

At Cloudflare, we believe in making our solutions easily integrate with the existing technology stack of our customers. Through our partnerships and integrations, we make it easier for our customers to use Cloudflare solutions jointly with that of partners, to further strengthen their security posture and unlock more value. Our partnership with CrowdStrike is an apt example of such efforts.
Together, Cloudflare and CrowdStrike are working to simplify the adoption of Zero Trust for IT and security teams. With this expanded partnership, joint customers can identify, investigate, and remediate threats faster through multiple integrations:
First, by integrating Cloudflare’s Zero Trust services with CrowdStrike Falcon Zero Trust Assessment (ZTA), which provides continuous real-time device posture assessments, our customers can verify users’ device posture before granting them access to internal or external applications.
Second, we joined the CrowdXDR Alliance in December 2021 and are partnering with CrowdStrike to share security telemetry and other insights to make it easier for customers to identify and mitigate threats. Cloudflare’s global network spans more than 250 cities in over 100 countries, blocking an average of 76 billion cyber threats each day. This provides customers with unparalleled insights, helping security teams better protect their organization. By joining the CrowdXDR Alliance, we will be able to use security signals from Cloudflare’s global network with CrowdStrike’s leading endpoint protection to help mutual customers stop cyber attacks anywhere in their network.
Third, CrowdStrike is one of Cloudflare’s incident response partners, providing rapid and effective support. CrowdStrike’s incident response team deals with active under attack situations day in, day out — helping customers mitigate the attack and get their web property and network back online. Our partnership with CrowdStrike enables rapid remediation of under attack scenarios to safeguard organizations from adversaries.
“The speed in which a company is able to identify, investigate and remediate a threat heavily determines how it will fare in the end. Our partnership with Cloudflare provides companies the ability to take action rapidly and contain exposure at the time of an attack, enabling them to get back on their feet and return to business as usual as quickly as possible.”
- Thomas Etheridge, Senior Vice President, CrowdStrike Services
CrowdStrike’s endpoint security meets Cloudflare’s Zero Trust Services

Before we get deep into how the integration works, let’s first recap Cloudflare’s Zero Trust Services.
Cloudflare Access and Gateway
Cloudflare Access determines if a user should be allowed access to an application or not. It uses our global network to check every request or connection for identity, device posture, location, multifactor method, and many more attributes to do so. Access also logs every request and connection — providing administrators with high-visibility. The upshot of all of this: it enables customers to deprecate their legacy VPNs.
Cloudflare Gateway protects users as they connect to the rest of the Internet. Instead of back hauling traffic to a centralized location, users connect to a nearby Cloudflare data center where we apply one or more layers of security, filtering, and logging, before accelerating their traffic to its final destination.
Zero Trust Integration with CrowdStrike
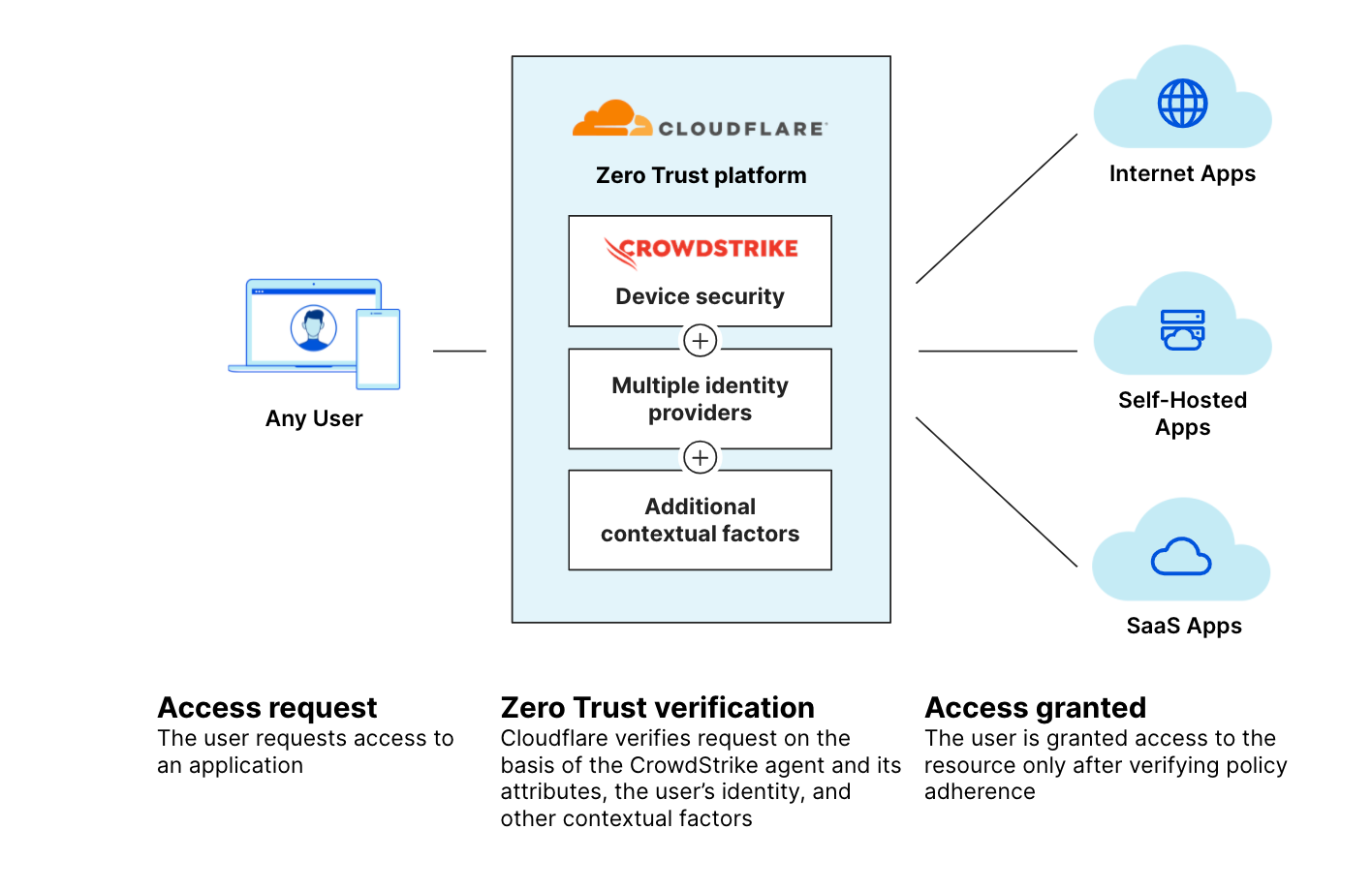
Cloudflare’s customers can now build Access and Gateway policies based on the presence of a CrowdStrike agent at the endpoint. In conjunction with our Zero Trust client, we are able to leverage the enhanced telemetry that CrowdStrike provides surrounding a user’s device.
CrowdStrike’s Zero Trust Assessment (ZTA) delivers continuous real-time security posture assessments across all endpoints in an organization regardless of the location, network or user. The ZTA scores enable enforcement of conditional policies based on device health and compliance checks to mitigate risks. These policies are evaluated each time a connection request is made, making the conditional access adaptive to the evolving condition of the device.
With this integration, organizations can build on top of their existing Cloudflare Access and Gateway policies ensuring that a minimum ZTA score or version has been met before a user is granted access. Because these policies work across our entire Zero Trust platform, organizations can use these to build powerful rules invoking Browser Isolation, tenant control, antivirus or any part of their Cloudflare deployment.
"The CrowdStrike Falcon platform secures customers through verified access controls, helping customers reduce their attack surface and simplify, empower and accelerate their Zero Trust journey. By expanding our partnership with Cloudflare, we are making it easier for joint customers to strengthen their Zero Trust security posture across all endpoints and their entire corporate network."
- Michael Sentonas, Chief Technology Officer, CrowdStrike
How the integration works
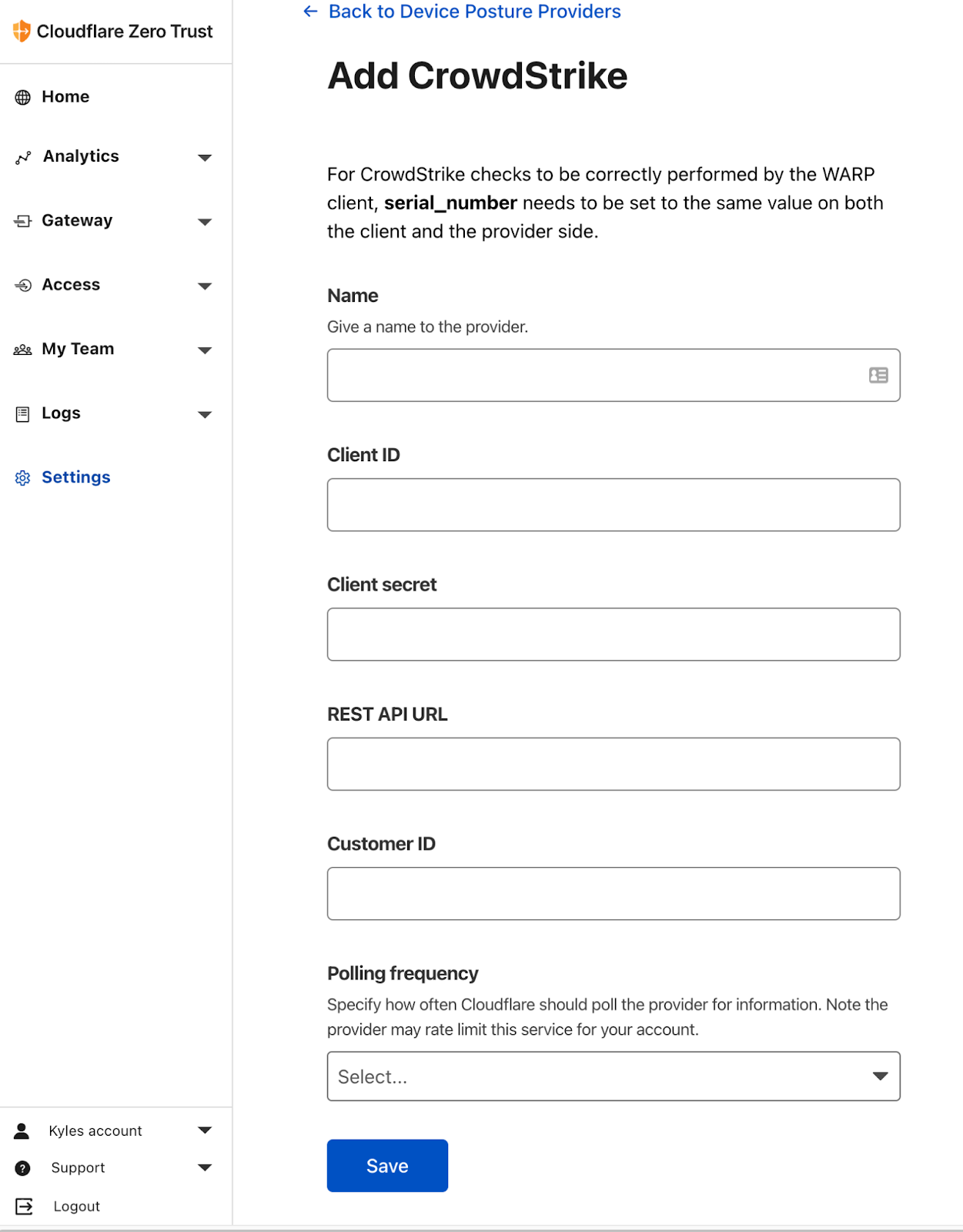
Customers using our Zero Trust suite can add CrowdStrike as a device posture provider in the Cloudflare Zero Trust dashboard under Settings → Devices → Device Posture Providers. The details required from the CrowdStrike dashboard include: ClientID, Client Secret, REST API URL, and Customer ID.
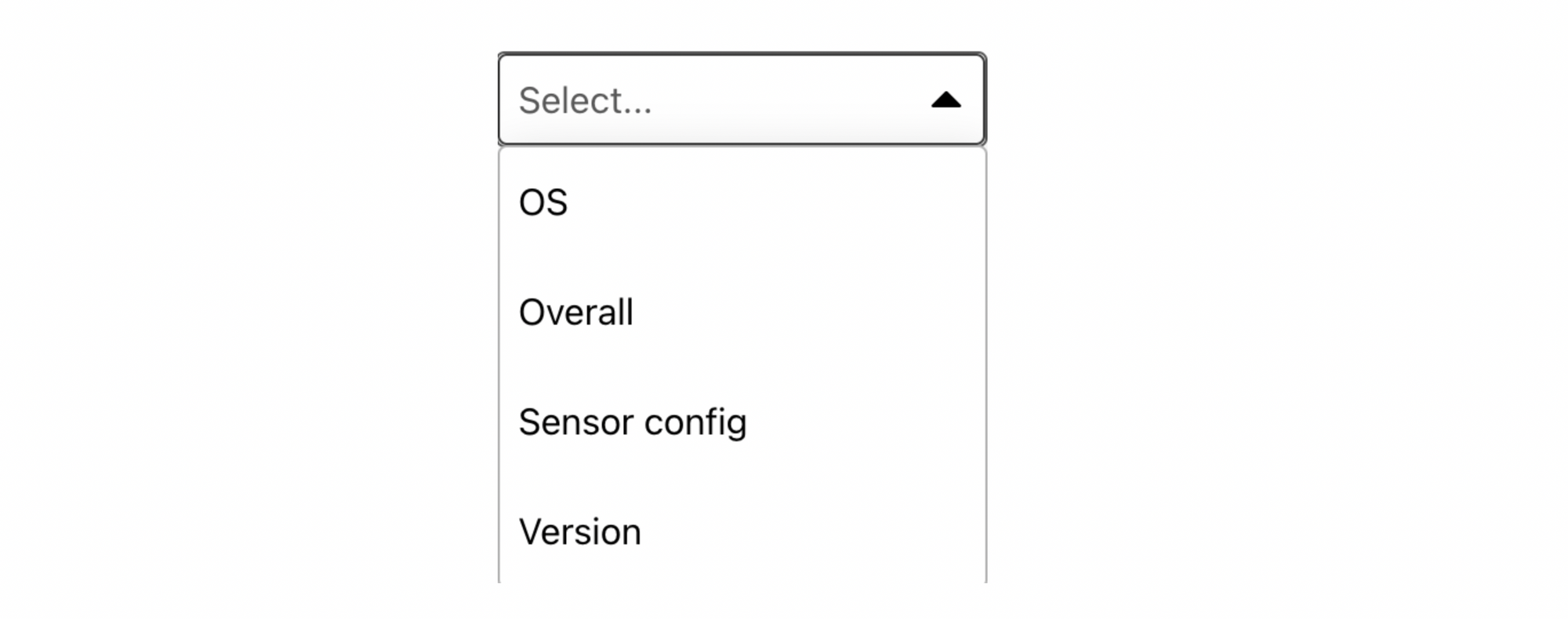
After creating the CrowdStrike Posture Provider, customers can create specific device posture checks requiring users’ devices to meet a certain threshold of ZTA scores.
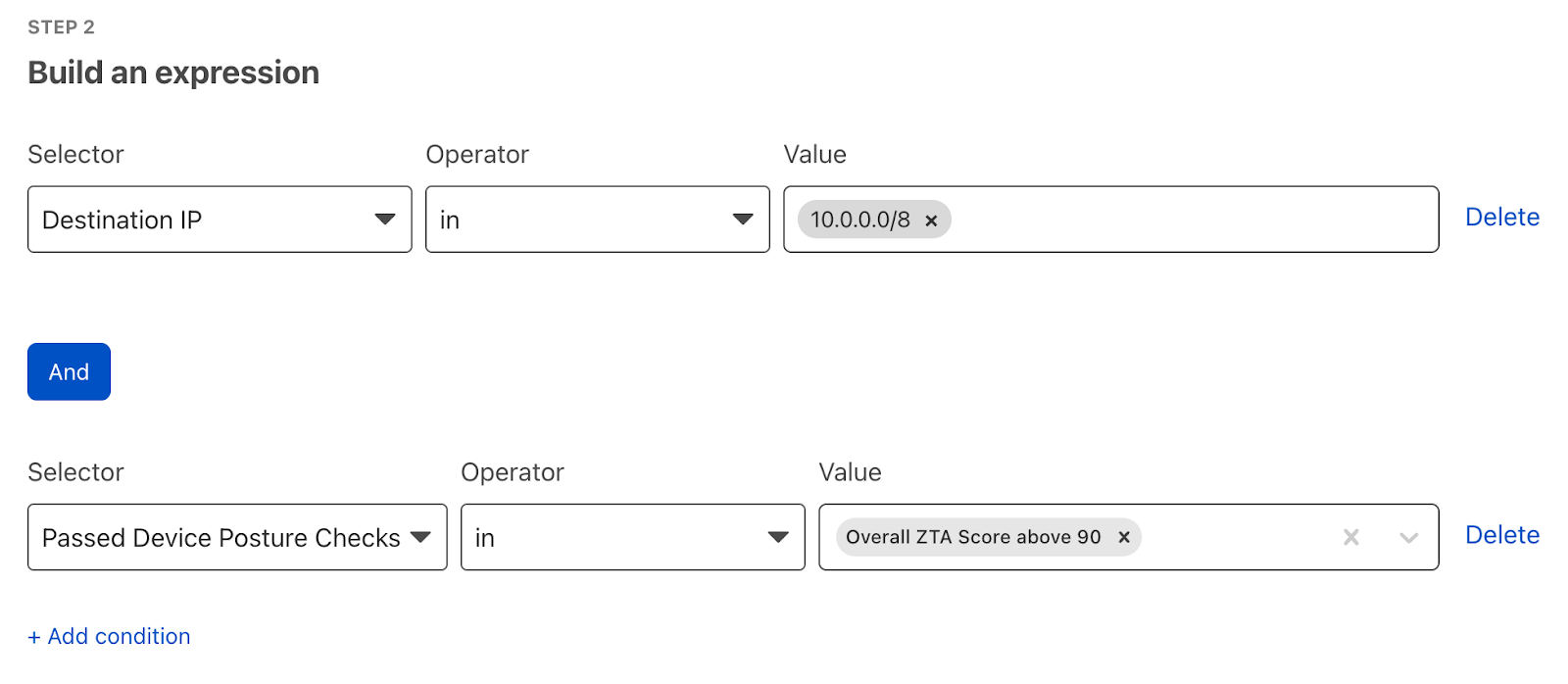
These rules can now be used to create conditional Access and Gateway policies to allow or deny access to applications, networks, or sites. Administrators can choose to block or isolate users or user groups with malicious or insecure devices.
What comes next?
In the coming months, we will be further strengthening our integrations with CrowdStrike by allowing customers to correlate their Cloudflare logs with Falcon telemetry, for timely detection and mitigation of sophisticated threats.
If you’re using Cloudflare Zero Trust products today and are interested in using this integration with CrowdStrike, please visit our documentation to learn about how you can enable it. If you want to learn more or have additional questions, please fill out the form or get in touch with your Cloudflare CSM or AE, and we'll be happy to help you.


